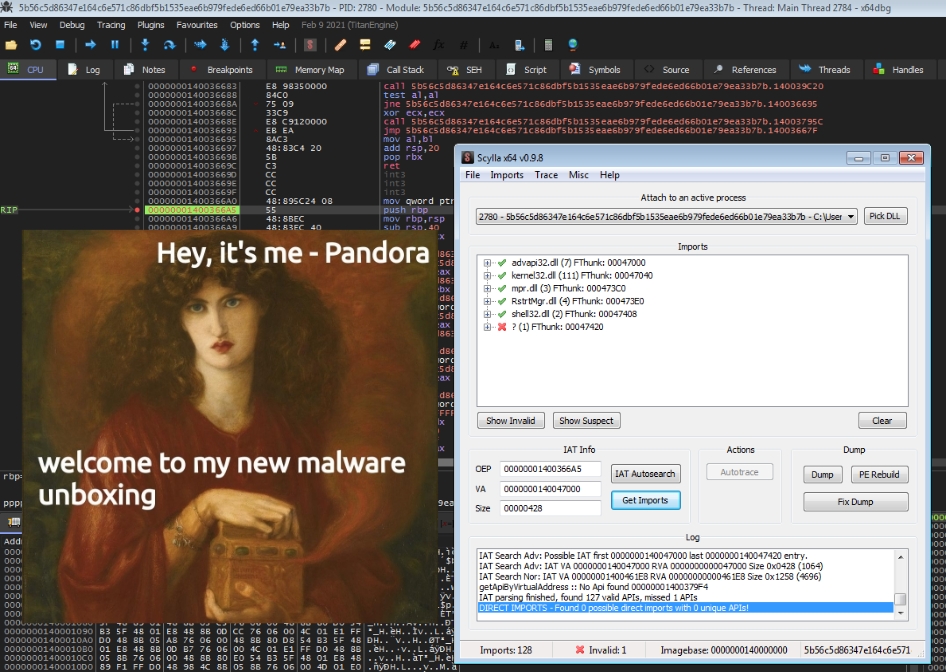
Quick revs: Pandora Ransomware - The Box has been open for a while...
Hey there, I’m finally getting around to introducing the new post category “Quick revs”, which will feature short write-ups of various malware …

Hey there, I’m finally getting around to introducing the new post category “Quick revs”, which will feature short write-ups of various malware …

Hey there, it has been a while, again.. 😅 This year was pretty stressful for me so far, so I didn’t really have the time to write about malware deep …

Hey there, long time no blog post :D It’s not like I haven’t been doing any research the last couple of months, but between the whole Covid-19 …
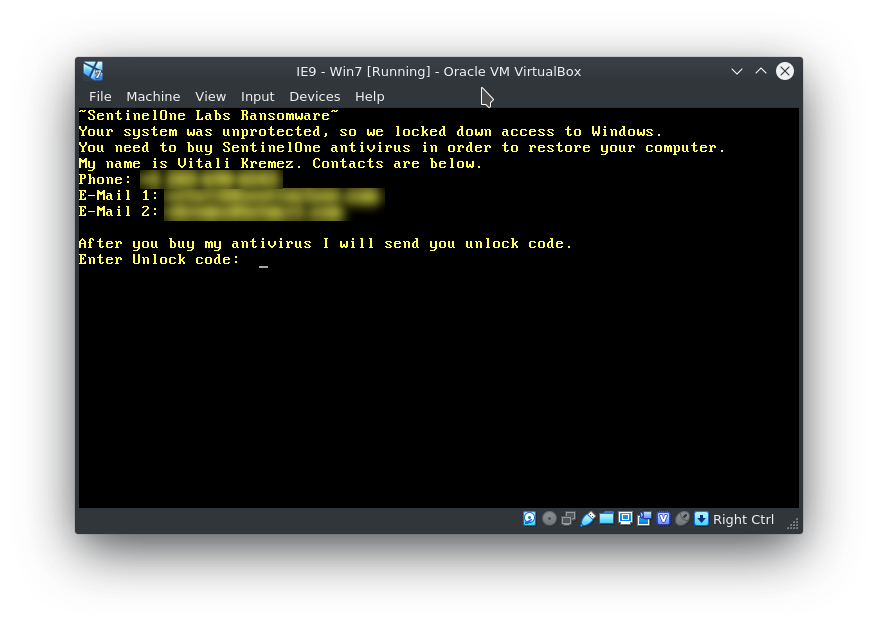
Let’s start right off with a short introduction: The Malware analyzed here is a so-called MBR (Master Boot Record) Locker. It is targeting (like most …
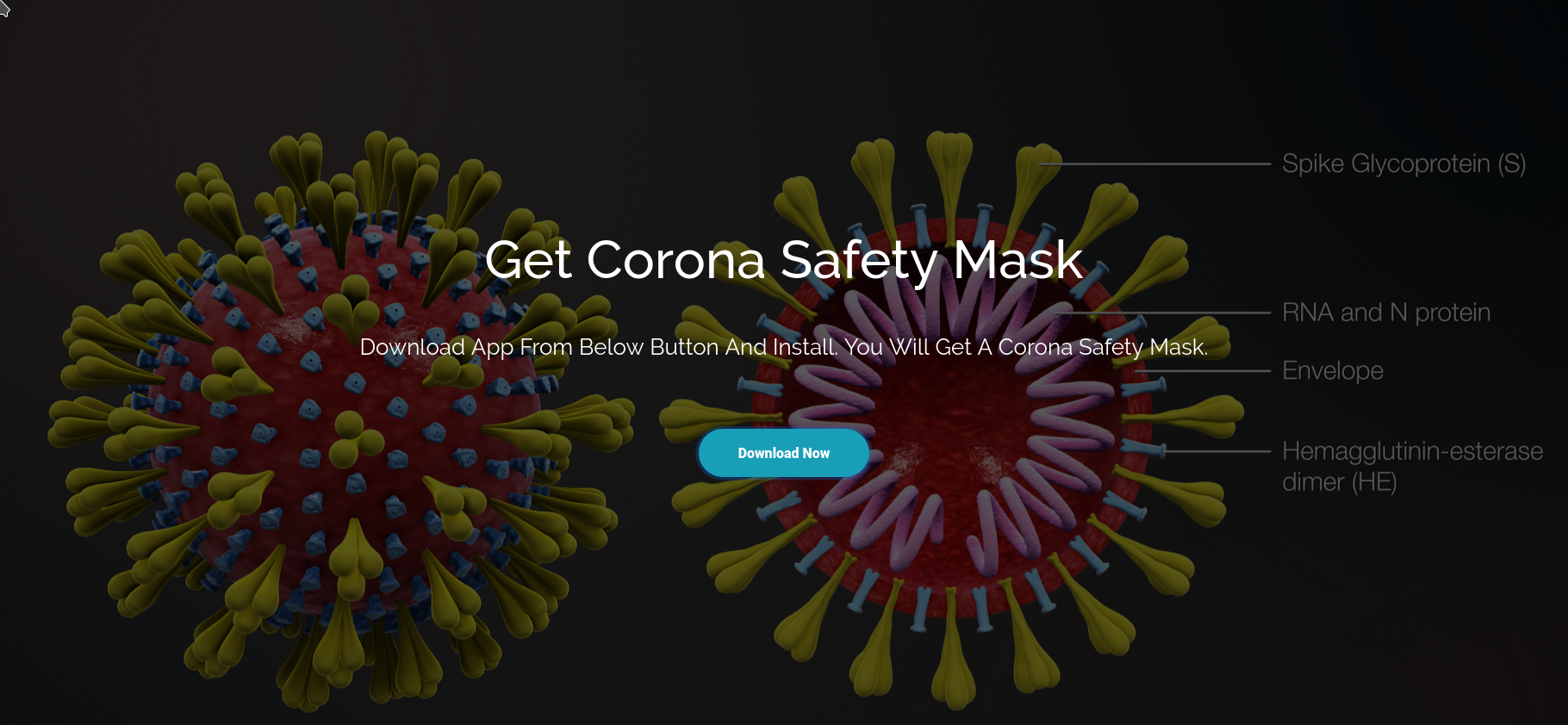
Since the current COVID-19 outbreak is getting masively taken advantage of by various cybercriminals I thought it would be a good opportunity to try …