Depending on the licensing model and capabilities Remcos is sold for 58$ to 389$ by the company (with the pretty fitting name) Breaking Security. Feature-wise the manfacturer's website lists: Remote Administration, Support, Surveillance, Anti-Theft and Proxy. In most cases the executable is dropped via a boobytrapped Office or XML Document. Of course I will not link to any of their webpages or products since shilling out for cybercriminals would be the last thing I'd do.

Inspiration for this blog post came from @wwp96 on Twitter:
#remcos
— wwp96 (@wwp96) September 7, 2019
jkharding2014.myddns[.]rocks
tomharry.ddns[.]net
2c8b1cca4ee54428dffc203b76c4dc30 - Dhl protected.iso
06469856a9bdecae989b64daf9db09c7 - carved exehttps://t.co/YtsJYbhle9
Remcos uses a Control instance (the C&C) and the so-called Agent (the executable that is delivered to the victim). It was first spotted in 2016 when it was being sold on HackForums. Since then it was being used in targeted attacks (mostly spear-phishing) against turkish government/military contractors or other businesses/individuals in the European Union. The Agent is written in C++ (while the Control application is written in Borland Delphi) and is 110KB in size. Click here for the AnyRun Analysis.
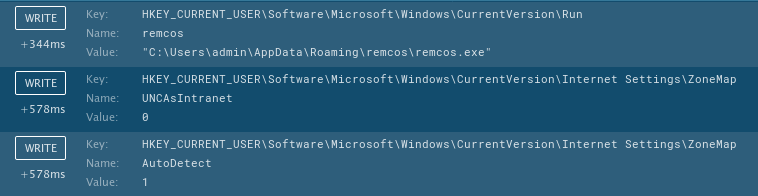
Of course it fiddles around in the registry as well. It uses the Key in HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run to bind to the system startup.
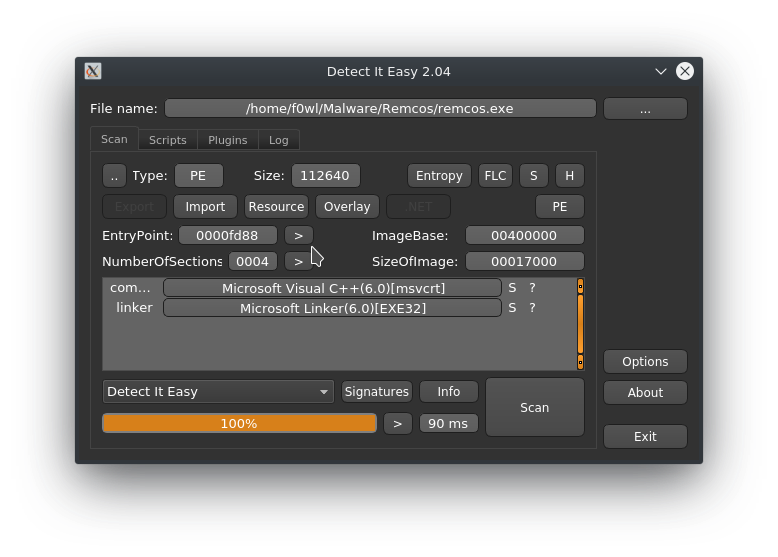
Although there are versions of Remcos that are packed with UPX and MPRESS1 this sample is not obfuscated in any way.

In terms of network interactions it queries two Dynamic DNS URLs that both point to the same host at 66.154.113[.]142
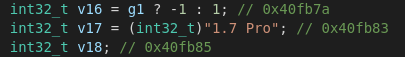
With Version 1.7 Pro we've got an old Version of the RAT in our hands which dates back to 5th of January 2017. The most recent version of the malware according to the changelog is V2.4.7. Another thing one usually doesn't get with malware: a 31-page manual. It goes over the features and configuation points the malware has to offer and even includes a "Terms of Service" chapter which states that users have to be notified that there is surveillance software in place and that the use of remcos for illegal activities is forbidden. As if they would care that their software was probably used in >95% of malicious acts. Judging by the typos and a few screenshots I'd attribute this malware to eastern european threat-actors.

The following Screenshots were captured after decompiling the executable with the retargetable Decompiler retdec by Avast. The decompiled result can be found here.
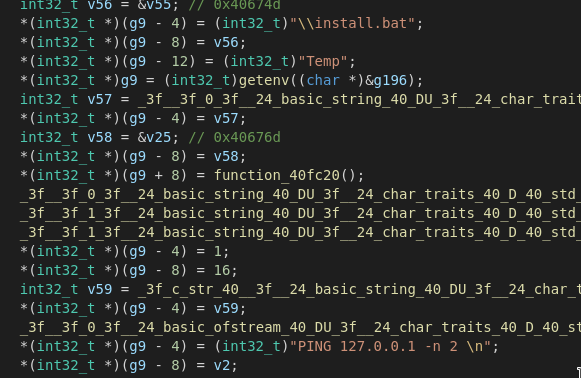
As a first step it runs its dropped install script called install.bat and uses a ping to localhost to stall the process and make sure it is finished before proceding.
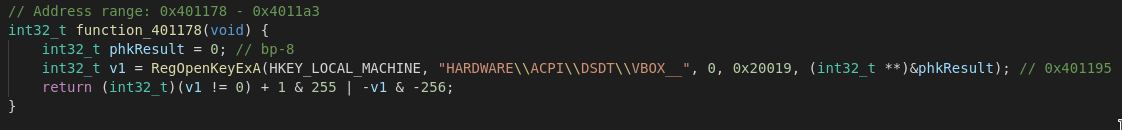
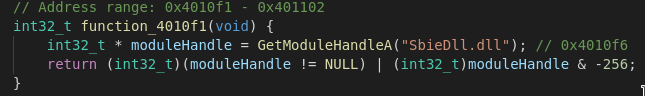
In terms of Evasion techniques Remcos turns up with detection methods for both Virtualbox and Sandboxie.The above example shows the method it employs for Virtualbox via a registry key that is set if the Guest Additions are in place on the guest system. In the same manner it tries to call SbieDll.dll to check if Sandboxie is present.
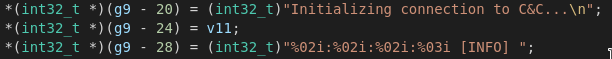
The Remcos Agent also has debugging functionality via a console window, for example for the communication with the C&C Server.
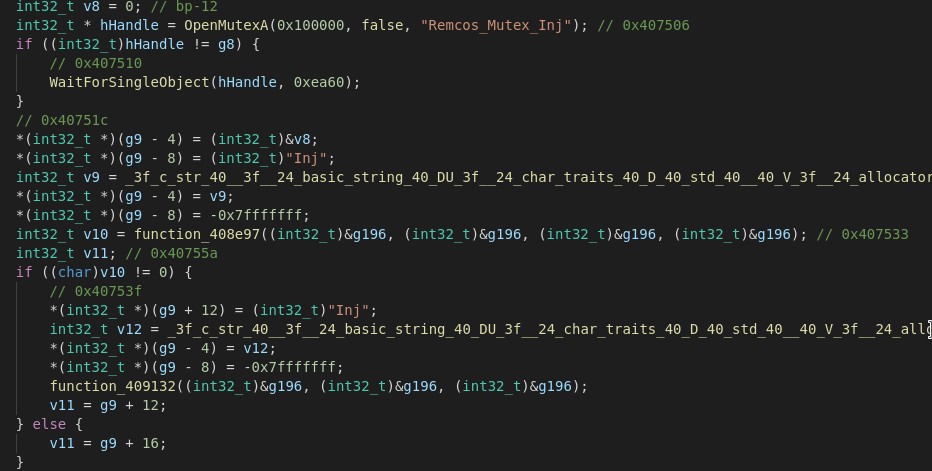
Remcos also employs Process Injection via a static Mutex. This behaviour is often used as a simple way of achieving persistence and to decrease the risk of a possible detection. Most versions of the RAT seem to inject into svchost.exe.
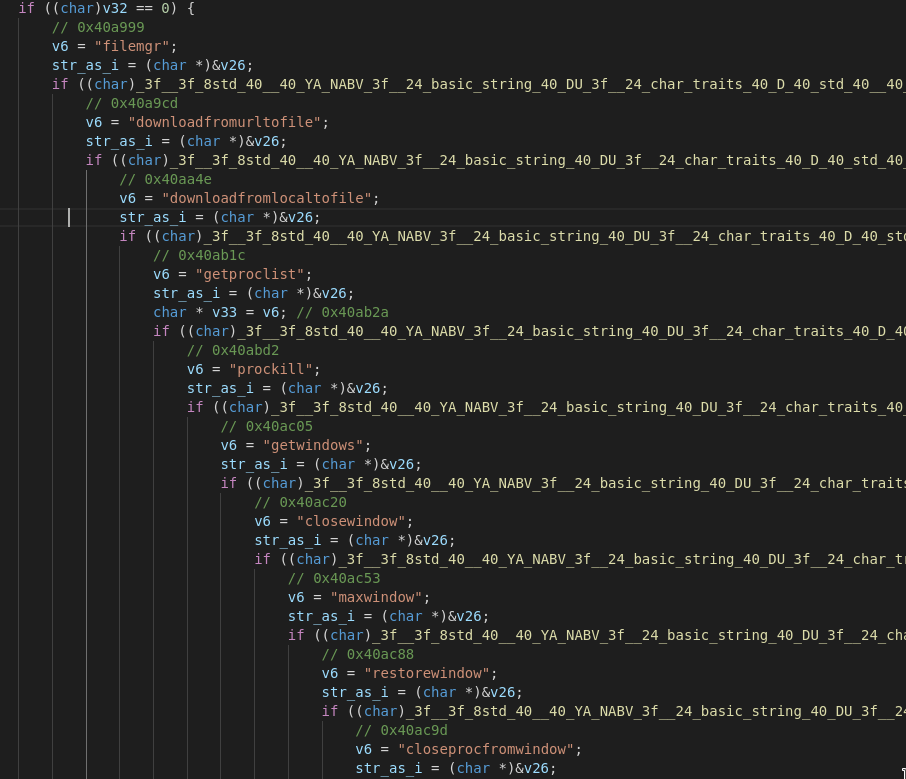
Via the command & control structure we also get a pretty good look at all the features the malware supports. In this screenshot we can see the file operations, process manipulations and window interactions it has to offer to the operator.
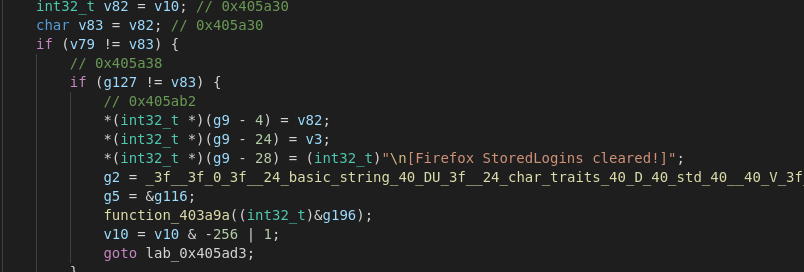
Another "standard" feature for RATs is accessing Browser History, cache and password stores. In this case Remcos is trying to manipulate user data in Mozilla Firefox.
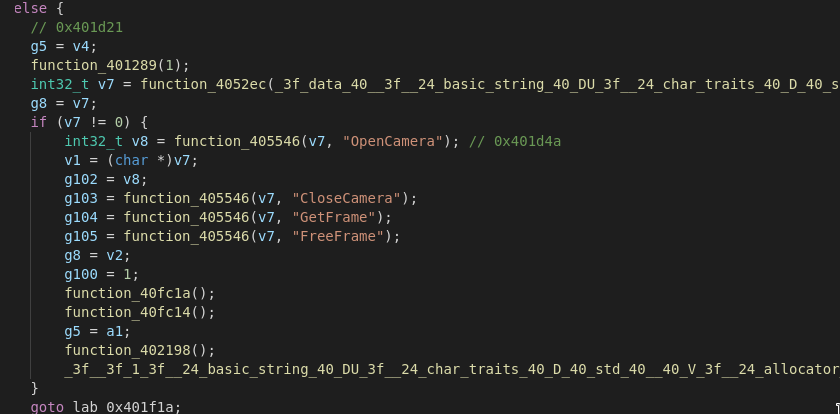
We also get a Look at the webcam capture module of the RAT which seems to support different camera modes. Additionally it also supports audio capture via a built-in microphone.
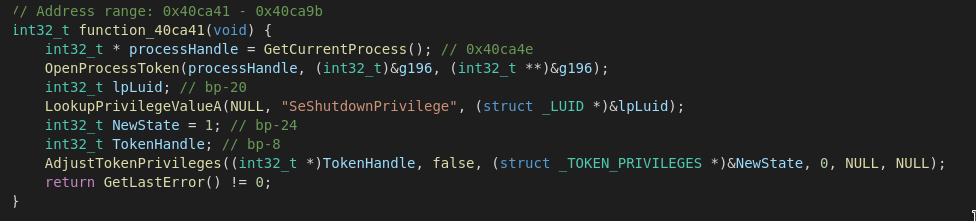
Lastly the malware also has the capabilities to manipulte the system power state depending on the current priviledges.
Although Remcos is not a "new" malware by today's definition it is still a serious threat to look out for. In my test it scores 53/68 on VirusTotal.
IOCs
Remcos RAT (SHA256)
1c3a298dd32da9de457842613dd4f07e0e57131a94bc13d868ffcbbebfab6d63
11535ea0ba3bf9ed0691b850955ef2613475dfdce7d8a32fa3d2d7ae066de73d
C&C URLs
httx://tomharry.ddns[.]net
httx://jkharding2014.myddns[.]rocks
httx://gratefulheart.ddns[.]net
httx://uaeoffice999.warzonedns[.]com
IPs
66.154.113[.]142
79.134.225[.]77
79.134.225[.]81
Modified Registry Keys
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
remcos --> "C:\Users\admin\AppData\Roaming\remcos\remcos.exe"
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap
UNCAsIntranet --> 0
AutoDetect --> 1

