
Sality @ AnyRun | HybridAnalysis | VirusTotal
--> sha256 37f1b6394a408e0a959b82ff118a526c1362b4ddc1db5da03c9ffa70acaebff4
To all Pinebook Users that may be affected by this Malware: It will not pose any threat to the notebook itself. It will however, potentially infect Windows machines that mount the eMMC storage (which is not a common use case). To remove Sality simply run a system upgrade or run this script manually.
On the 3rd of November it was first publicly disclosed by stheo on Twitter that there were unidentified Windows-related files on the boot partition of Pinebook Pro. As the Discussion in the Discord/IRC Chat evolved it became clear that only the second batch (the 64GB eMMC Versions) of the Notebook has to be infected. The initial VirusTotal Analysis revealed that the Files in question were related to the Sality Botnet. Calling this a "supply chain attack" is also pretty clickbaity (I'm sorry :D), but what it boils down to is, that one or more flashing stations in the Factory in China have been infected with Sality. These systems often run outdated software (in this case probably XP or older) and have poor security standards.
@thepine64 Why do I have a malware called “yvyfr.exe” with an autorun.inf on my boot partition of my Pinebook Pro ? I have no Windows at home and it’s a fresh install and update of the Pinebook Pro.
— studer (@stheo) November 3, 2019
VT analysis : https://t.co/Hne9BR15vQ pic.twitter.com/zIHz7sm6VB
After recieving my Pinebook I immediately opened the Dolphin Filemanager to check /boot and sure enough, there were two files with seemingly random filenames ending in .pif and an autorun.inf file. The other files in this directory are not affiliated with the Sality Botnet: rk3399-pinebookpro.dtb is the DTS file, Image contains the Kernel (for both of these files there are possibly also Backup files present, marked with a .bak suffix) and the extlinux directory contains files related to the bootloader.
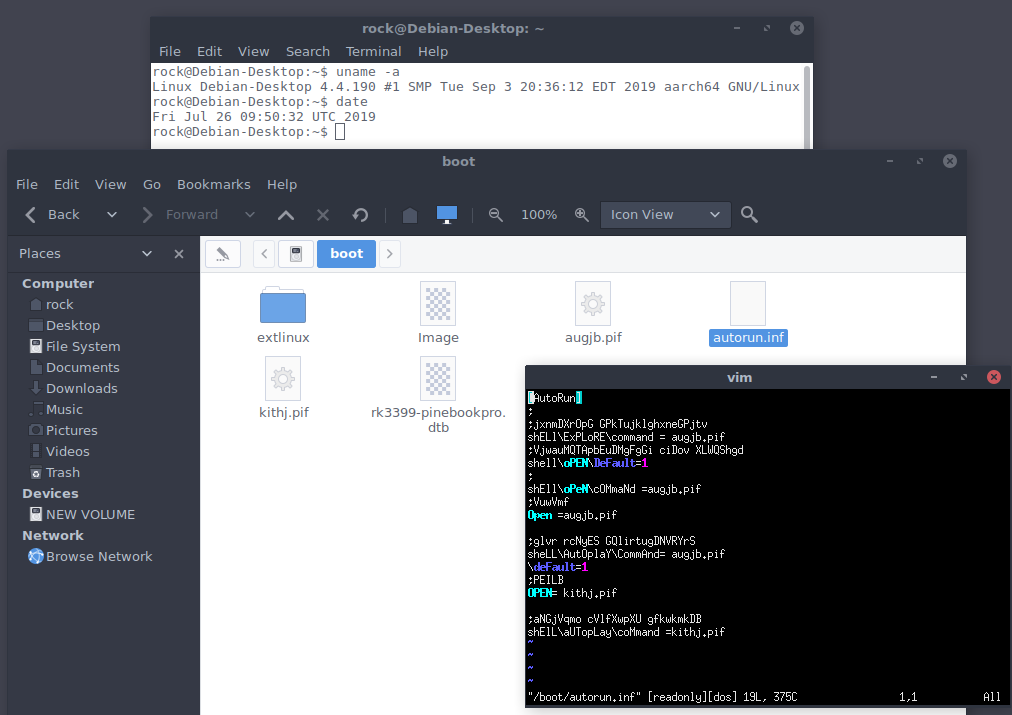
I haven't seen a pif file in a pretty long time, so I had to refresh my memory a bit as well. PIF stands for "Program information file" and describes certain environmental conditions and settings for a given application. In modern versions of windows this information is stored in .LNK Files. So does it contain shell commands similar to how the GermanWiper stage 1 worked? Quoting Wikipedia here:
"Although a file in PIF format does not contain any executable code (it lacks executable files' magic number "MZ"), Microsoft Windows handles all files with (pseudo-)executables' extensions in the same manner: all .COMs, .EXEs, and .PIFs are analyzed by the ShellExecute function and will run accordingly to their content and not extension, meaning a file with the PIF extension can be used to transmit computer viruses."
Sounds really interesting 🤔 So let's throw it into a Hex Editor and ... wait is that a MZ-Header? Looks like we've got an executable here after all.
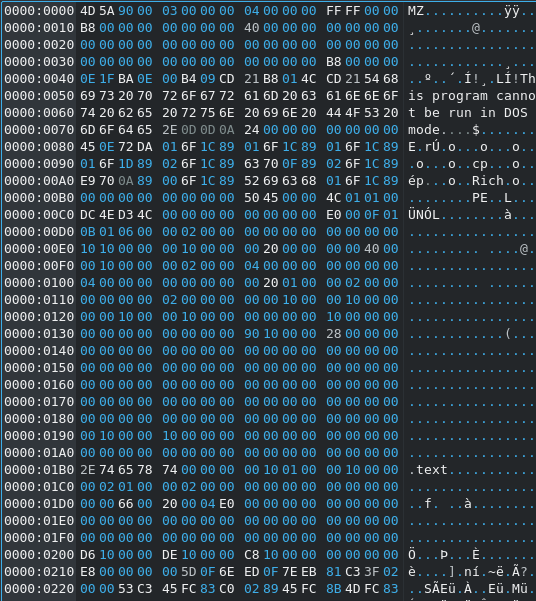
It also looks like at least one of the two EXEs has been padded quite heavily.
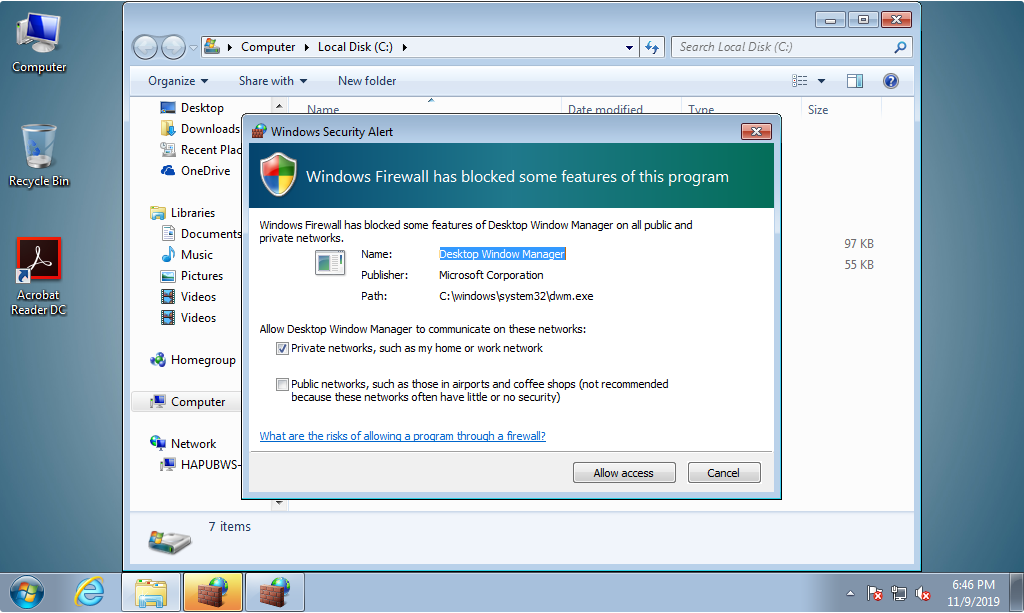
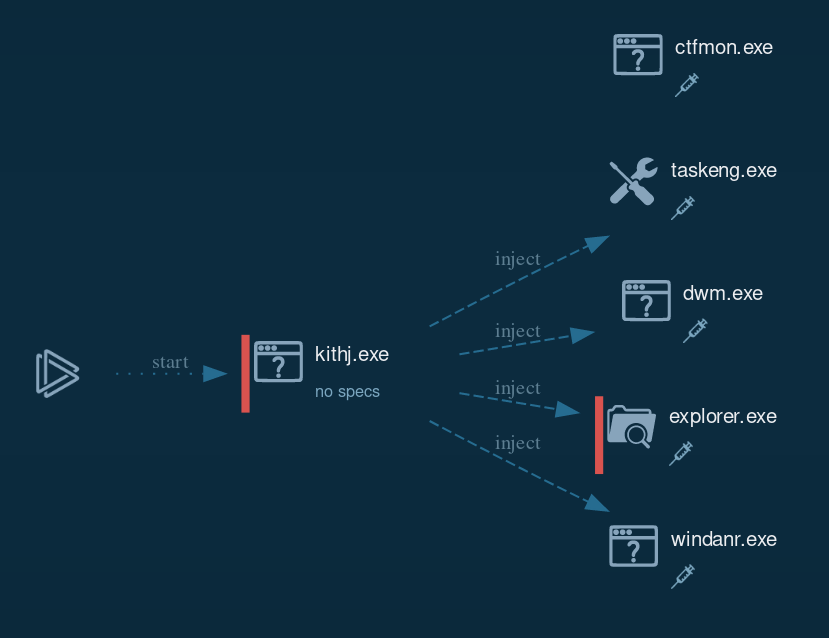
Running kithj.exe in AnyRun with standard UAC settings results in the Malware requesting access via injecting into the Desktop Window Manager Process to run at an elevated level and look more legit.
Looking at the Process Graph we notice multiple process injections into various system applications (namely the Windows Explorer, Desktop Window Manager, Task Scheduler and WindaNr).
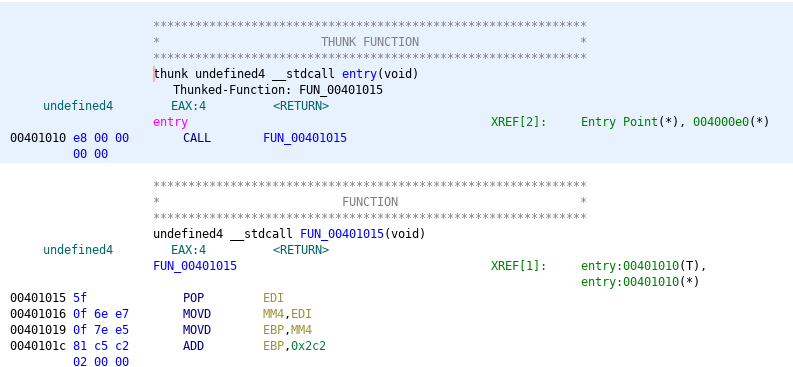
Ghidra can't make much of it with the standard analysis settings and can only find two "functions" in total.
IOCs
Sality Hashes
kithj.exe --> SHA256: 37f1b6394a408e0a959b82ff118a526c1362b4ddc1db5da03c9ffa70acaebff4
SSDEEP: 3072:m5y36RPOJTdktKKu37BLgwl7gMt7pwObB:mQqRQydiBLJl7Jt7N
augjb.exe --> SHA256: 6245eb607e53209126191e4b6cdf7d64f52394f6bc6a2a9529a28ed49be19c82
SSDEEP: 3072:EE6sGYXKm+NFN3GtRM0XS0aGNH3MYaOJEQ/Xh6:AsqdWdbaG8YOcx6
autorun.inf --> SHA256: f5adcd0989f9c4033fcd214e8998dde85865c6bf178c4eaed94128e6f5389bd6
Associated Files
augjb.pif(.exe)
kithj.pif(.exe)
autorun.inf
URLs
hxxp://padrup[.]com.ds/sobaka1.gif
hxxp://paaaaad[.]fd.fd
IPs of contacted Hosts
IP - Port - exclusively UDP
118.136.16.138 - 5614
180.247.53.107 - 7866
86.107.231.10 - 7534
93.114.69.232 - 5684
220.247.166.100 - 4492
202.177.246.59 - 6715
189.122.188.39 - 7538
89.38.237.65 - 5064
188.215.25.69 - 6310
14.96.75.194 - 6130
212.76.78.10 - 6260
14.98.120.25 - 6740
112.204.145.248 - 5300
200.8.145.17 - 6780

