
This strain was first discovered by Korben Dallas on Twitter on the 9th of January. As I already mentioned the Malware is delivered via a Malspam/Maldoc attack crafted for Users / Companies from Croatia. Researchers that were involved in the initial analysis: @KorbenD_Intel, @James_inthe_box, @Malwageddon, @pollo290987 and I (@f0wlsec). Thank you for your contributions!
@James_inthe_box @malwrhunterteam @Malwageddon
— Korben Dallas (@KorbenD_Intel) January 9, 2020
69450923d812f3696e8280508b636955 XLS 12/60 VT scan detections. Not nice.. upped to Malshare: https://t.co/jXxXrJxcB9 pic.twitter.com/TPfP0BCZOB
A general disclaimer as always: downloading and running the samples linked below will lead to the encryption of your personal data, so be f$cking careful. Also check with your local laws as owning malware binaries/ sources might be illegal depending on where you live.
Afrodita @ AnyRun | VirusTotal | HybridAnalysis
--> sha256 9b6681103545432cd1373492297a6a12528f327d14a7416c2b71cfdcbdafc90b
Here you can see three images extracted from the malicious Excel Docs. Funny how they didn't even bother to think of a fake company name for the second Logo :D

Afrodita uses a sleep routine for Sandbox evasion. In my Tests it took 30-60mins until the system was infected.
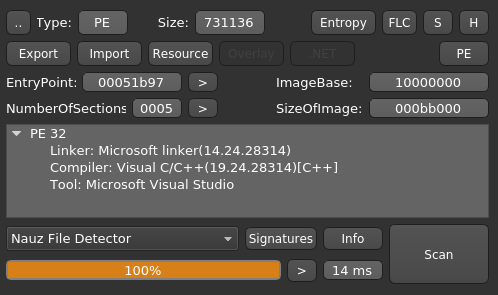
After unpacking the sample with UPX, Detect it easy returns the following:
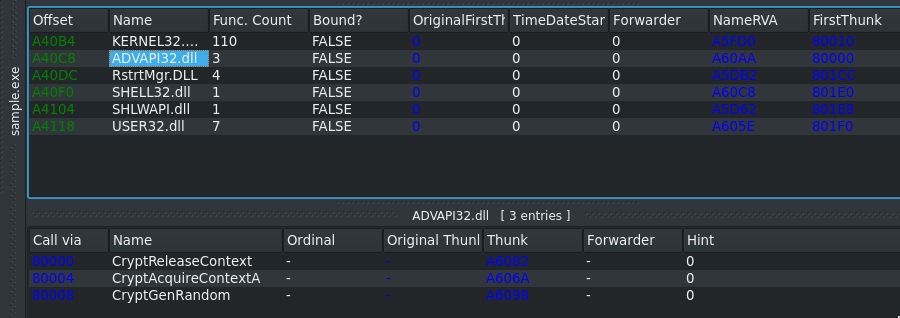
Below you can see a screenshot of PEBear from the Imports-Tab.
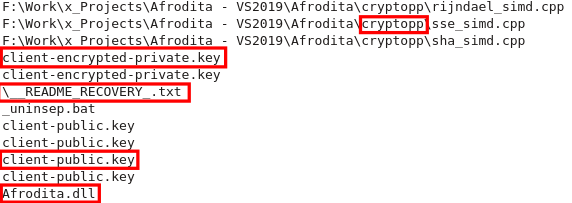
The extracted strings tell us quite a lot in this case. It looks like the internal name of the Project is Afrodita and it utilizes the CryptoPP Library. There are some references to .key files, but I haven't found a path or file on a infected machine yet. README_RECOVERY .txt is will be the filename of the Ransomnote. It's contents are embeded in the binary's .data section with Base64 encoding. Lastly Afrodita.dll is the rewritten file that is downloaded as a payload (originally notnice.jpg or verynice.jpg). It's executed via rundll32.exe Afrodita.dll,Sura.
The following filetypes will be encrypted by Afrodita:
.TXT, .ZIP, .DAT, .JPE, .JPG, .PNG, .JPEG, .GIF, .BMP, .EXIF, .MP4, .RAR, .M4A, .WMA, .AVI, .WMV, .MKV, .CSV, .M3U, .FLV, .WALLET, .JAVA, .CLASS, .HTML, .HTM, .CSS, .LUA, .ASP, .PHP, .INCPAS, .ASM, .HPP, .CPP, .SLN, .ACCDB, .MDB, .PPTM, .PPTX, .PPT, .XLK, .XLSB, .XLSM, .XLSX, .XLS, .WPS, .DOCM, .DOCX, .DOC, .ODB, .ODC, .ODM, .ODP, .ODS, .ACCDR, .ACCDT, .ACCDE, .D3DBSP, .SIE, .SQL, .BACKUPDB, .BACKUP, .BAK, .SUM, .IBANK, .T13, .T12, .QDF, .GDB, .TAX, .PKPASS, .SLDM, .SLDX, .PPSM, .PPSX, .PPAM, .POTM, .POTX, .PPS, .POT, .XLW, .XLL, .XLAM, .XLA, .XLTM, .XLTX, .XLM, .XLT, .DOTM, .DOTX, .DOT, .BC6, .BC7, .BKP, .QIC, .BKF, .SIDN, .SIDD, .MDDATA, .ITL, .ITDB, .ICXS, .HVPL, .HPLG, .HKDB, .MDBACKUP, .SYNCDB, .GHO, .CAS, .SVG, .MAP, .WMO, .ITM, .FOS, .MOV, .VDF, .ZTMP, .SIS, .SID, .NCF, .MENU, .LAYOUT, .DMP, .BLOB, .ESM, .VCF, .VTF, .DAZIP, .FPK, .MLX, .IWD, .VPK, .TOR, .PSK, .RIM, .W3X, .FSH, .NTL, .ARCH00, .LVL, .SNX, .CFR, .VPP_PC, .LRF, .MCMETA, .VFS0, .MPQGE, .KDB, .DB0, .DBA, .ROFL, .HKX, .BAR. .UPK, .DAS, .IWI, .LITEMOD, .ASSET, .FORGE, .LTX, .BSA, .APK, .RE4, .SAV, .LBF, .SLM, .BIK, .EPK, .RGSS3A, .PAK, .BIG, .WOTREPLAY, .XXX, .DESC, .P7C, .P7B, .P12, .PFX, .PEM, .CRT, .CER, .DER, .X3F, .SRW, .PEF, .PTX, .R3D, .RW2, .RWL, .RAW, .RAF, .ORF, .NRW, .MRWREF, .MEF, .ERF, .KDC, .DCR, .CR2, .CRW, .BAY, .SR2, .SRF, .ARW, .3FR, .DNG, .CDR, .INDD, .EPS, .PDF, .PDD, .PSD, .DBF, .MDF, .WB2, .RTF, .WPD, .DXG, .DWG, .PST, .ODT, .DXF, .MP3,.MRW, .NEF, .JFIF, .DRF, .BLEND, .APJ, .3DS, .SDA, .PAT, .FXG, .FHD, .DXB, .DRW, .DESIGN, .DDRW, .DDOC, .DCS, .CSL, .CSH, .CPI, .CGM, .CDX, .CDRW, .CDR6, .CDR5, .CDR4, .CDR3, .AWG, .AIT, .AGD1, .YCBCRA, .STX, .ST8, .ST7, .ST6, .ST5, .ST4, .SD1, .SD0, .RWZ, .RA2, .PCD, .NWB, .NOP, .NDD, .MOS, .MFW, .MDC, .KC2, .IIQ, .GRY, .GREY, .GRAY, .FPX, .FFF, .EXF, .DC2, .CRAW, .CMT, .CIB, .CE2, .CE1, .3PR, .MPG, .SQLITEDB, .SQLITE3, .SQLITE, .SDF, .SAS7BDAT, .S3DB, .RDB, .PSAFE3, .NYF, .NX2, .NX1, .NSH, .NSG, .NSF, .NSD, .NS4, .NS3, .NS2, .MYD, .KPDX, .KDBX, .IDX, .IBZ, .IBD, .FDB, .ERBSQL, .DB3, .DB-JOURNAL, .CLS, .BDB, .ADB, .MONEYWELL, .MMW, .HBK, .FFD, .DGC, .DDD, .DAC, .CFP, .CDF, .BPW, .BGT, .ACR, .AC2, .AB4, .DJVU, .SXM, .ODF, .MSG, .STD, .SXD, .OTG, .STI, .SXI, .OTP, .ODG, .STC, .SXC, .OTS, .SXG, .STW, .SXW, .OTH, .OTT
The Ransomware encrypts the first 512 Bytes of the File Header which will render most filetypes useless. It does not leave any Signature in the data of the files and neither does it append a custom extension to the filename.

Another IOC: It creates the following Mutex: 835821AM3218SAZ
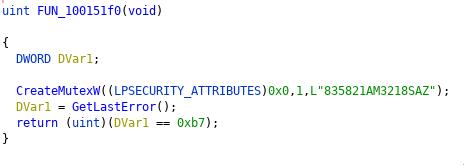
Update 10.01.2020:
The criminals obviously failed to properly display the key / victim ID in the Ransomnote. This was also a problem because the screwed encoding killed this Blogs Atom RSS Feed :D To resolve this issue I removed the malformed section from this page. If you want to have a look at the original note plus a couple of encrypted jpegs, download the zip file.
Also this Malware family isn't as new as I originally thought. According to Michael Gillespie the MalwareHunterTeam found the first Maldoc in Late November. A few days later Checkpoint research found it as well:
#Afrodita Ransomware, appears to be a new strain.
— Check Point Research (@CPResearch) December 3, 2019
Targeting businesses in Croatia via legitimate looking Excel spreadsheets.
Subject: “Poziv na placanje”
DZ: http://content-delivery[.]in/verynice.jpg
XLSM: 597ec6887f3bcdc5077939bdf1fb69f1
DLL: ebacbff99234887d9f27719e48bafe59 pic.twitter.com/IM0h4fHUDT
Today Michael also asked if anyone was able to parse the main-public.key because the format seems off. I extracted it from the binary:
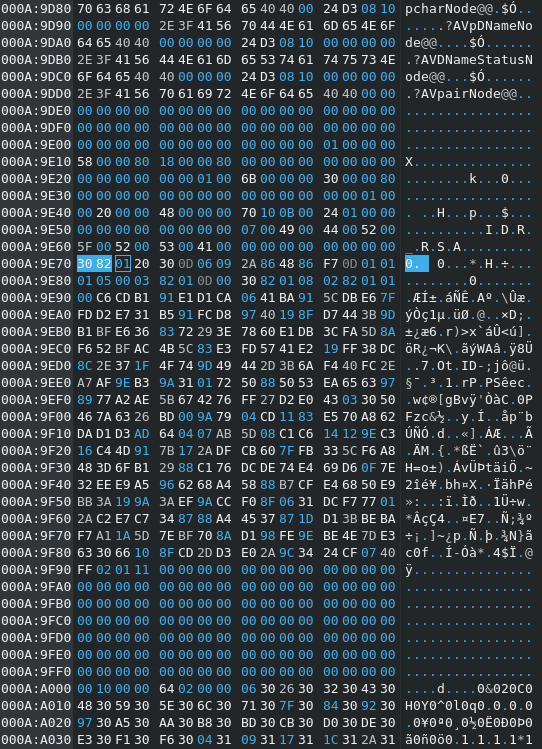
A quick look into the CryptoPP Wiki revealed that the key was in raw (uncooked) ASN.1 format (you can identify it by hex 30 82). Using an online ASN.1 decoder (Link) yields us the public key:

-----BEGIN RSA PUBLIC KEY-----
MIIBIDANBgkqhkiG9w0BAQEFAAOCAQ0AMIIBCAKCAQEAxs2xkeHRygZBupFc2+Z//dLnMbWR/NiXQBmP
10Q7nbG/5jaDcik+eGDh2zz6XYr2Ur+sS1yD4/1XQeIZ/zjcjC43H090nUlELTtq9ED8LqevnrOaMQFy
UIhQU+plY5eJd6KuW2dCdv8n0uBDAzBQRnpjJr0AmnkEzRGD5XCoYtrR061kBAerXQjBxhQSnsMWxE2R
excq38tgf/szXPaoSD1vsSmIwXbc3nTkadYPfjLu6aWWYmikWIi3z+RoUOm7OhmaOu+azPCPBjHc93cB
KsLnxzSHiKRFN4cd0Tu+uvehGl1+v3CK0Zj+nr5OfeNjMGYQj80t0+AqnDQkzwdA/wIBEQ==
-----END RSA PUBLIC KEY-----
MITRE ATT&CK
T1179 --> Hooking --> Persistence
T1179 --> Hooking --> Privilege Escalation
T1045 --> Software Packing --> Defense Evasion
T1179 --> Hooking --> Credential Access
T1114 --> Email Collection --> Collection
IOCs
Afrodita
notnice.jpg --> SHA256: 9b6681103545432cd1373492297a6a12528f327d14a7416c2b71cfdcbdafc90b
SSDEEP: 6144:EXrm0zIiAhjC7Cqa5ZhiIJDQ13Xdksm1Cx2tJk:EbNQaCq6iIJcdksmJtJ
Payload Servers
hxxp://riskpartner[.]hr/wp-content/notnice.jpg
hxxp://content-delivery[.]in/verynice.jpg
E-Mail Addresses / Contact
afroditateam@tutanota.com
afroditasupport@mail2tor.com
hxxps://t[.]me/RecoverySupport
Ransomnote
~~~ Greetings ~~~
[+] What has happened? [+]
Your files are encrypted, and currently unavailable. You are free to check.
Every file is recoverable by following our instructions below.
Encryption algorithms used: AES256(CBC) + RSA2048 (military/government grade).
[+] Guarantees? [+]
This is our daily job. We are not here to lie to you - as you are 1 of 10000's.
Our only interest is in us getting payed and you getting your files back.
If we were not able to decrypt the data, other people in same situation as you
wouldn't trust us and that would be bad for our buissness --
So it's not in our interest.
To prove our ability to decrypt your data you have 1 file free decryption.
If you don't want to pay the fee for bringing files back that's okey,
but remeber that you will lose a lot of time - and time is money.
Don't waste your time and money trying to recover files using some file
recovery "experts", we have your private key - only we can get the files back.
With our service you can go back to original state in less then 30 minutes.
[+] Service [+]
If you decided to use our service please follow instructions below.
Contact us:
Install Telegram(available for Windows,Android,iOS) and contact us on chat:
Telegram contact: https://t.me/RecoverySupport
Also available at email afroditateam@tutanota.com cc: afroditasupport@mail2tor.com
Make sure you are talking with us and not impostor by requiring free 1 file decryption to make sure we CAN decrypt!!
[Removed victim ID because it breaks the RSS Feed :D]
Title Image by Robert Drózd, modified

