
A general disclaimer as always: downloading and running the samples linked below will lead to the encryption of your personal data, so be f$cking careful. Also check with your local laws as owning malware binaries/ sources might be illegal depending on where you live.
medusa.exe @ AnyRun
--> sha256 3a5b015655f3aad4b4fd647aa34fda4ce784d75a20d12a73f8dc0e0d866e7e01
dix_16.exe @ HybridAnalysis
--> sha256 49da42d00cc3ad6379ead2e07fd5f09bd358b144a6e78aad4bb1a8298e2bb568
Taking a look at the stringdump that stringsifter produced one of the first things that stood out was this base64 encoded image:
After decoding it we get an image of a medieval pest doctor. Fun fact: They wore these masks because they thought it would protect them from the black death. One day someone will probably start selling these for endpoint protection.
Another interesting extracted string is this PDB-Path: C:\Users\Gh0St\Desktop\MedusaLockerInfo\MedusaLockerProject\MedusaLocker\Release\MedusaLocker.pdb
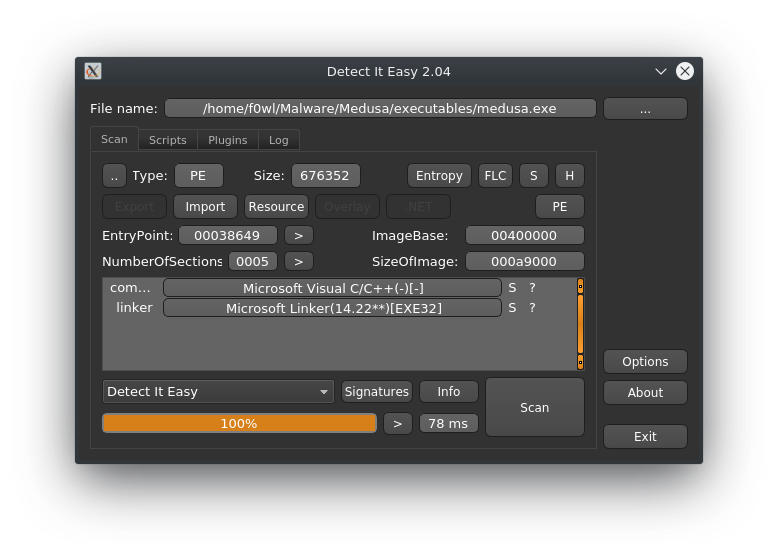
Running it through Detect it easy returns that MedusaLocker was built with Visual C++ and a (in malware-terms) relatively new Linker Version.
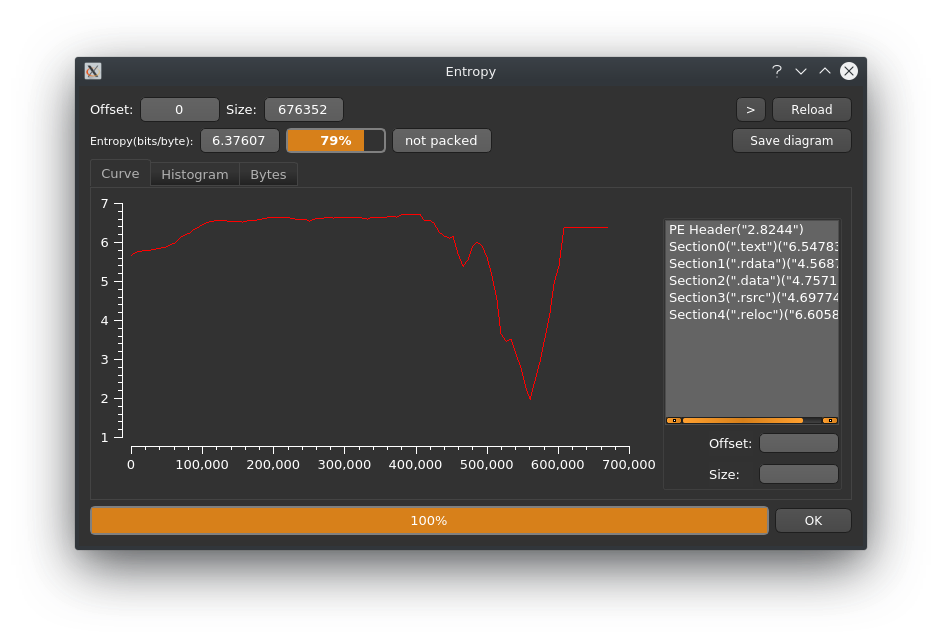
Entropy-wise it doesn't look like this sample is packed and the sections found don't look out of the ordinary either.
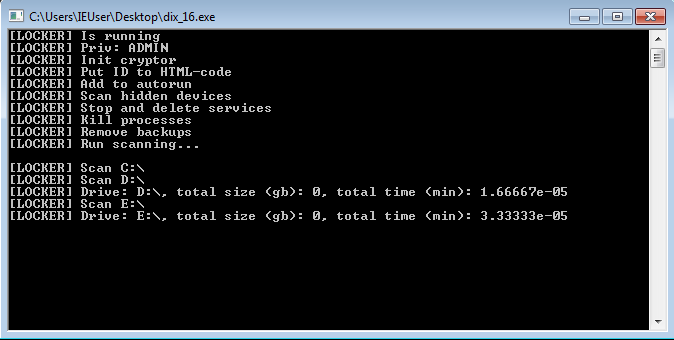
After digging around in Ghidra for a bit I found FUN_00405bc0 which seems to be the main program routine of MedusaLocker. The strings shown here match the output in the debug console present in the second sample discussed below.
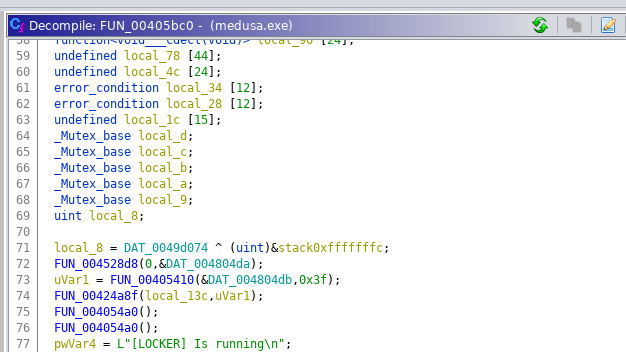
Yet another mysterious CLSID that I can't make sense of at the moment: {8761ABBD-7F85-42EE-B272-A76179687C63}. Search results referencing it are around since October 21st and might make tracking Medusa a bit easier.
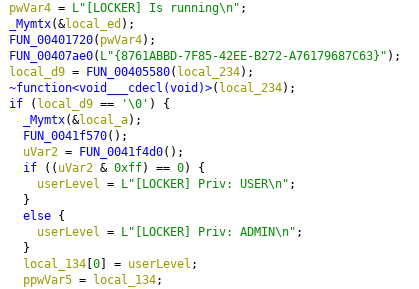
Next up the Locker will "initialize the crypto module" which uses CryptGenKey provided by WinCrypt to derive a keypair. I'll have a closer look at the encryption routine later.
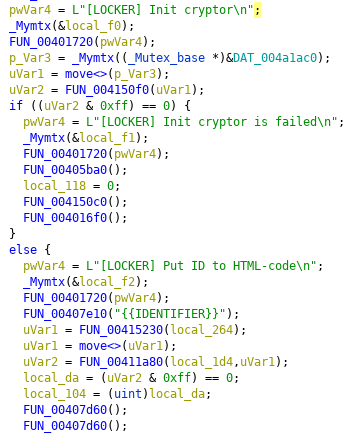
It will skip files with the following suffixes:
exe, dll, sys, ini, lnk, rdp, encryptedAs it is very popular with Ransomware to disable the Automatic Startup Repair and delete System Restore Points plus shadow copies Medusa will do so as well. After that it will also relanch LanmanWorkstation to ensure that mapped network drives are available.

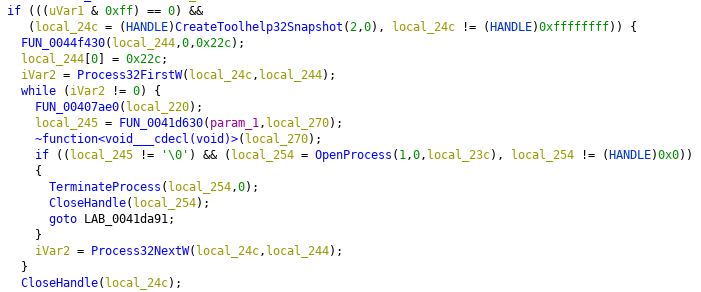
After the "Adding to Autoload" debug message it will rename itself to svchost.exe and add it's Registry Key to the System startup.

MedusaLocker will try to terminate the following processes by their name. The List contains Security Software as well as Services commonly used in productive environments such as SQL or Webservers.
wrapper, DefWatch, ccEvtMgr, ccSetMgr, SavRoam, sqlservr, sqlagent, sqladhlp, Culserver, RTVscan, sqlbrowser, SQLADHLP,
QBIDPService, Intuit.QuickBooks.FCS, QBCFMonitorService, sqlwriter, msmdsrv, tomcat6, zhudongfangyu, SQLADHLP,
vmware-usbarbitator64, vmware-converter, dbsrv12, dbeng8wxServer.exe, wxServerView, sqlservr.exe, sqlmangr.exe,
RAgui.exe, supervise.exe, Culture.exe, RTVscan.exe, Defwatch.exe, sqlbrowser.exe, winword.exe, QBW32.exe, QBDBMgr.exe,
qbupdate.exe, QBCFMonitorService.exe, axlbridge.exe, QBIDPService.exe, httpd.exe, fdlauncher.exe, MsDtSrvr.exe,
tomcat6.exe, java.exe, 360se.exe, 360doctor.exe, wdswfsafe.exe, fdlauncher.exe, fdhost.exe, GDscan.exe, ZhuDongFangYu.exe
It also copies itself to %APPDATA% after renaming to executable to "svchostt.exe".
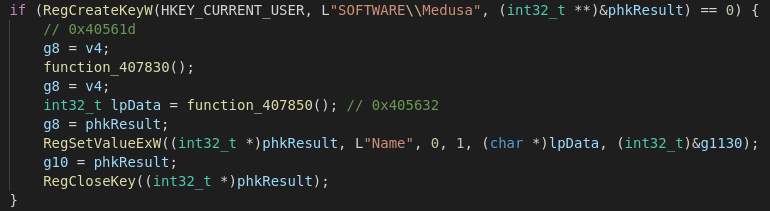
To check if an instance of MedusaLocker previously ran on the system it will create a Registry Key at HKEY_CURRENT_USER\Software\Medusa
Furthermore it tries to read the State of EnableLinkedConnections via RegOpenKeyExW(HKEY_LOCAL_MACHINE, L"SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System" ... and enables the key if necessary since Medusa tries to encrypt Shared Network Drives and removeable Media as well.

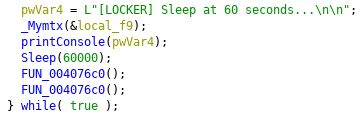
After terminating the encryption loop the Ransomware will wait for 60 seconds and start a new scan to check for new unencrypted files.
Running MedusaLocker in a VM yields us this UAC Prompt with a mysterious CLSID ({3E5FC7F9-9A51-4367-9063-A120244FBEC7}). A quick google search brings us to Wikileaks Page for the CIA Vault7 leaks and the ID seems to be corresponding to cmstplua.dll. Turns out this is an UAC bypass known and implemented since August 2017 (mentioned here).

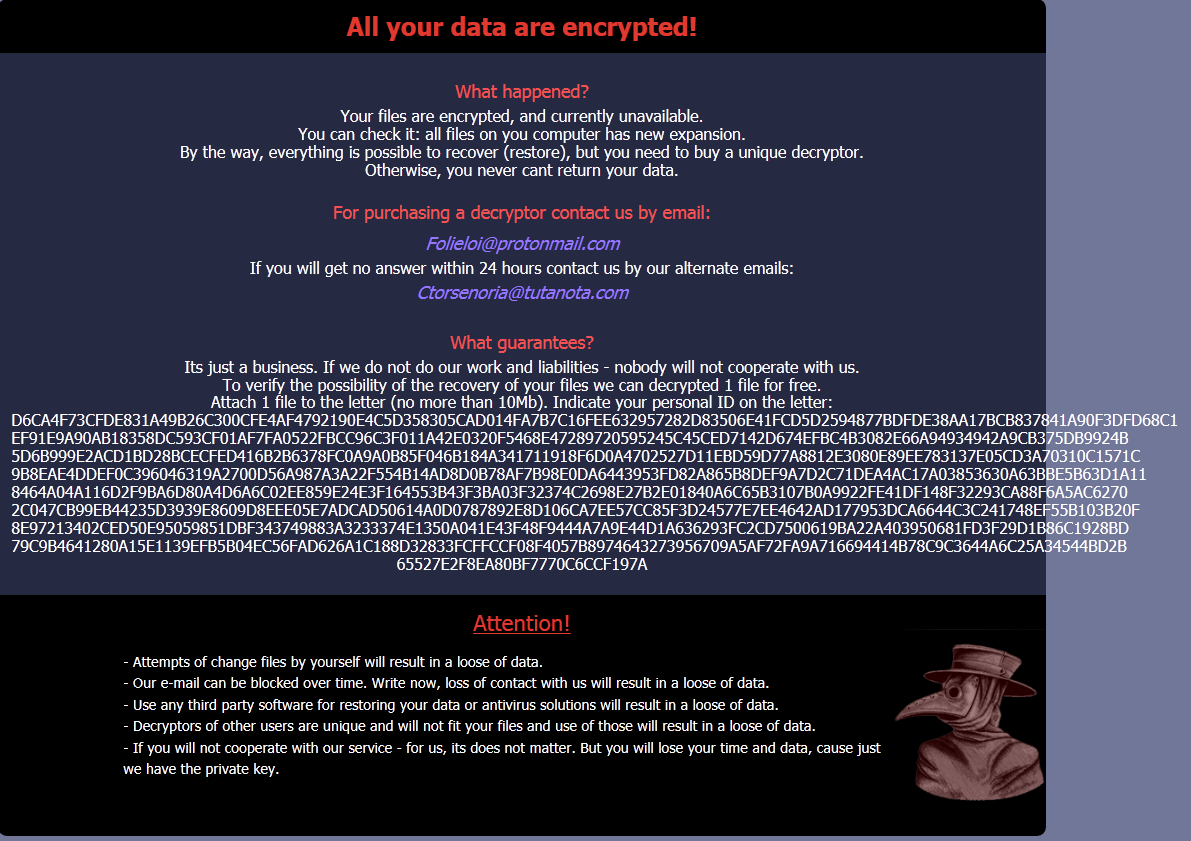
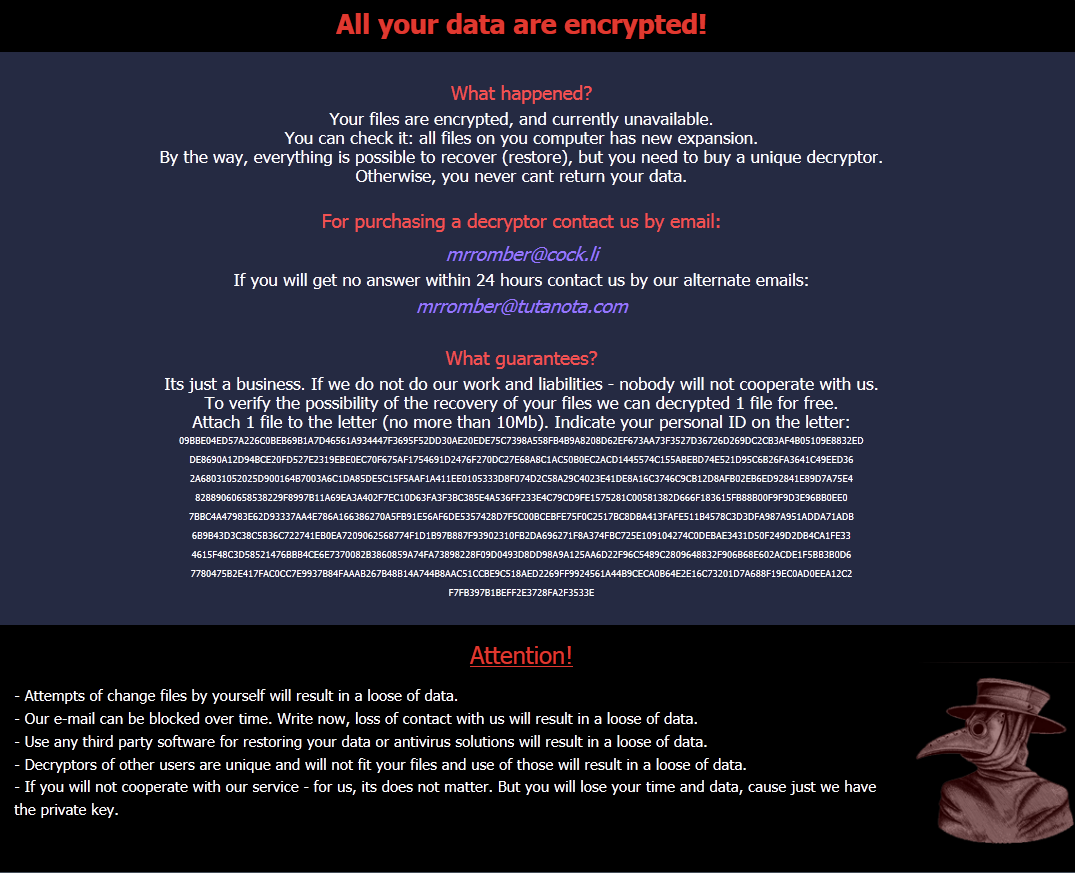
The Ransomnote (which is dropped in every directory that contains files to encrypt) is delivered as a HTML file. In this early sample they seem to have messed up their text alignment. This was fixed in a later version (see below) and will make it easier to identify new samples as they may appear.
Looking at the section list compared to the
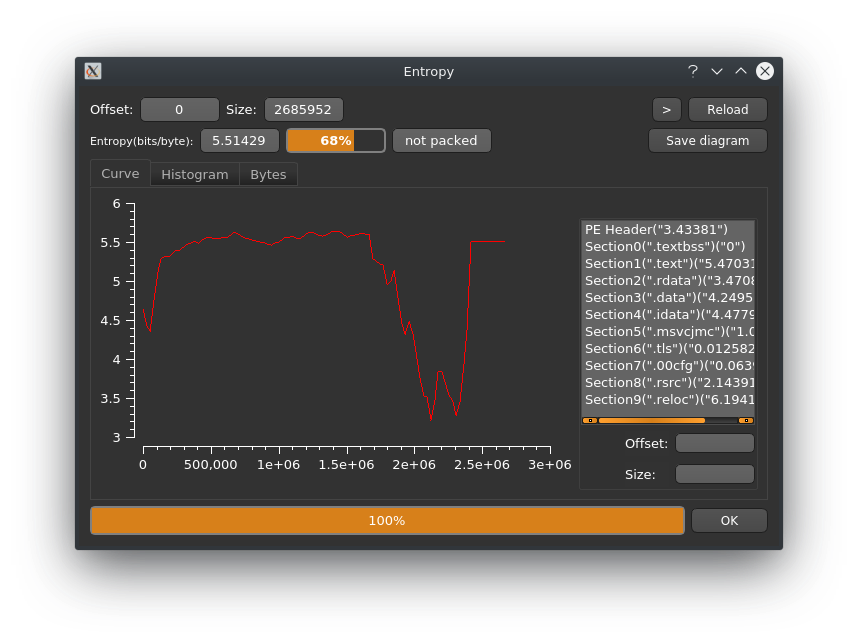
This sample seems to have an enabled debug console which allows us to trace the steps of the infection.
Below you can see the new ransomnote. The Protonmail E-Mail address was exchanged for a cock.li one and the Victim ID blob was fitted to the textbox.
BleepingComputer Forum User ttrifonov who was hit by the ransomware as well found suspicious files on his Desktop after the Infection took place. Fortunately for us Medusa skipped the executables.
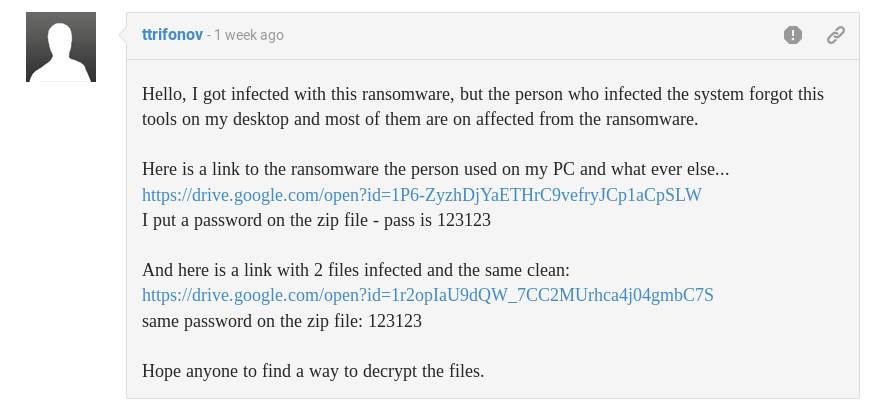
This would be a huge discovery infection vector-wise as this looks like the attacker gained access to the machine via RDP. (Yet another proof [if we would need any] that RDP exposed to the internet isn't a good idea)
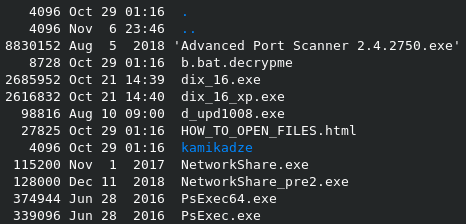
Looks like the attacker left a few files related to Mimikatz as well...

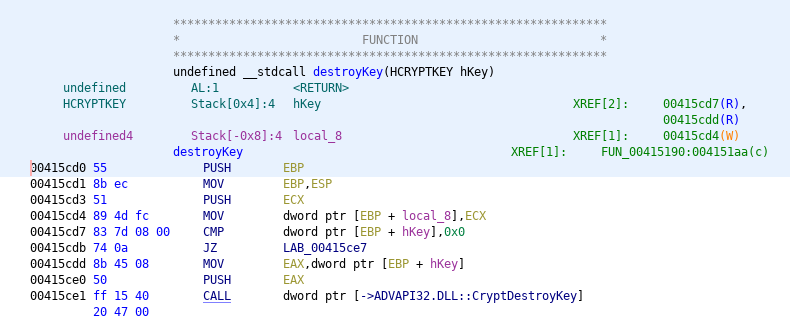
As I mentioned earlier the keypair is generated via CryptGenKey. I'm still trying to map out all the actions on the key material.
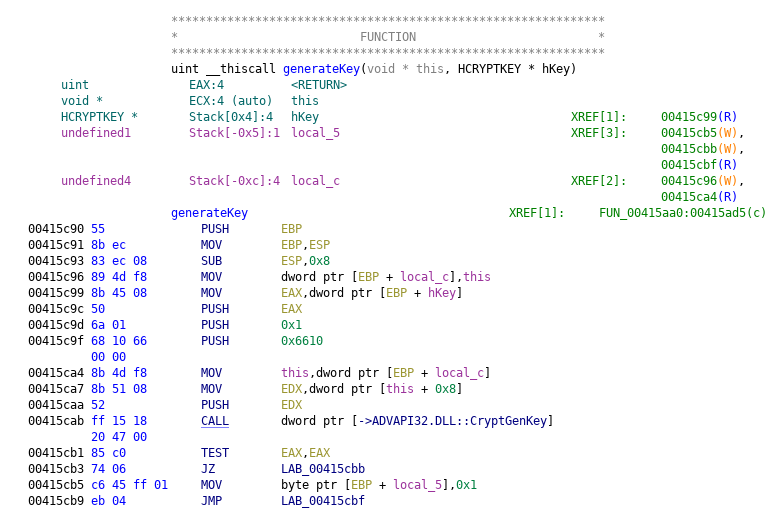
The encryption itself is done via the CryptEncrypt function. It seems to use AES for the files and then encrypts the key with a RSA-2048 public key that is stored via a keyblob in the executable.
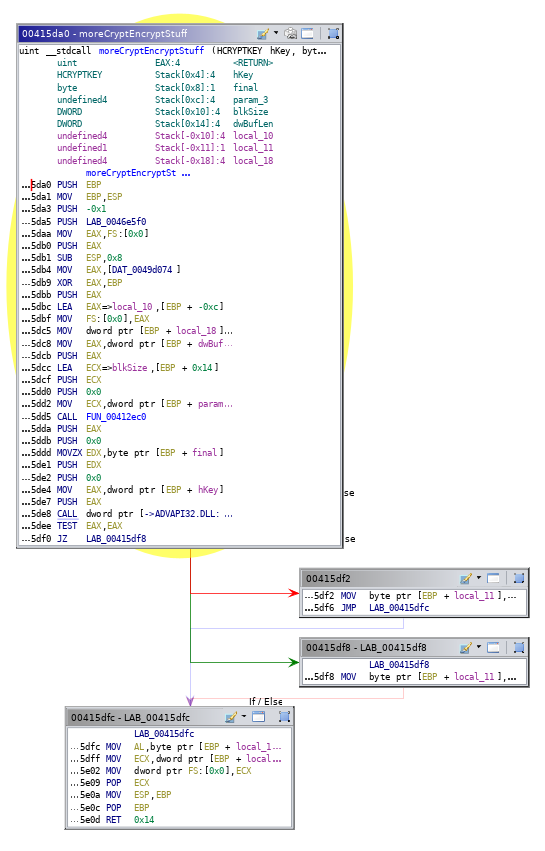
After the encryption routine is done the generated hKey is deleted via CryptDestroyKey.
Update 23.11.2019:
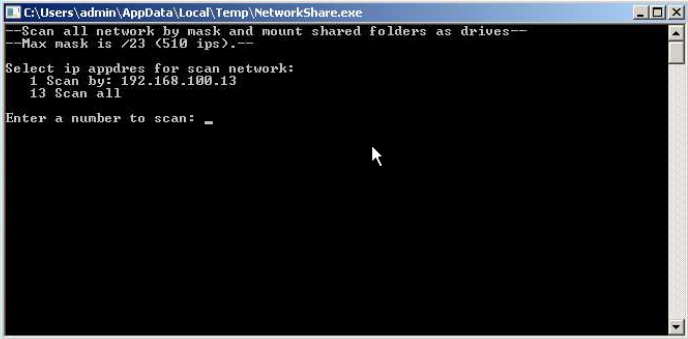
Now I want to take a closer look at the files left by the attacker on the Victim's Desktop as it was reported multiple times on the BleepingComputer Forum. Besides the Mimikatz files in the kamikadze directory there is a semi-legit tool called "Advanced Port Scanner" (AnyRun, which is basically just a garbage Zenmap alternative for Windows people) and another one called "NetworkShare.exe" (AnyRun, seems to scan for reachable network shares and tries to mount them).
It also looks like there's a dedicated version of MedusaLocker for Windows XP called dix_16_xp.exe. As you can see below the Debug Messages start with [LockerXP] instead of [Locker].

The Decryptor 🧐
The Decryptor is delivered per Machine with a 4 letter filename indicating to which victim ID it belongs.

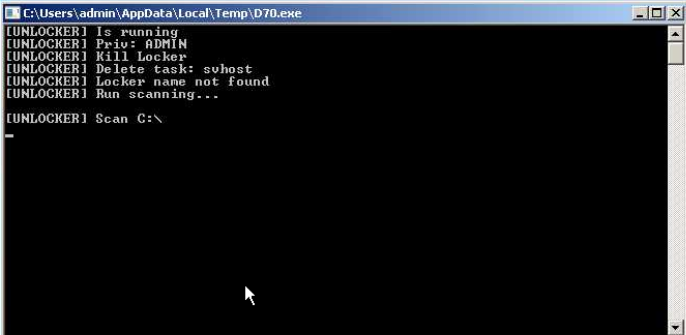
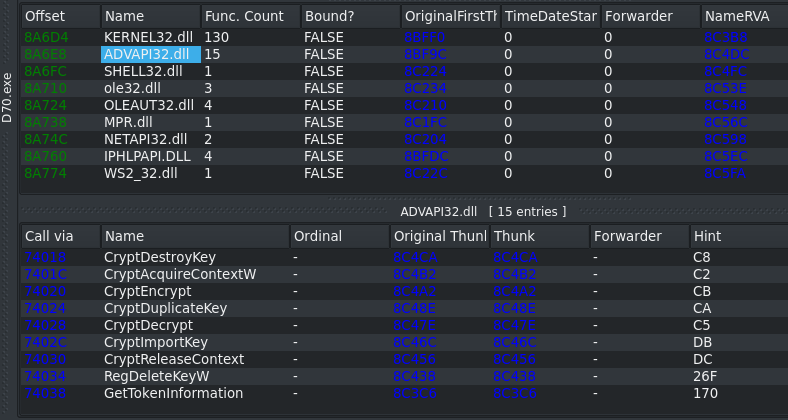
IOCs
Medusa (SHA256)
medusa.exe --> SHA256: 3a5b015655f3aad4b4fd647aa34fda4ce784d75a20d12a73f8dc0e0d866e7e01
SSDEEP: 12288:f+IZ+bobAyYFJPrsU4VwryxjpBx8ajiOhA8tsV1YRbRb7:2++EMyYFJPoUecOh8aWdD1UB7
dix_16.exe --> SHA256: 49da42d00cc3ad6379ead2e07fd5f09bd358b144a6e78aad4bb1a8298e2bb568
SSDEEP: 24576:nJC1YAOp0eRaNaQgxPubcoiukAby3LV1jqjx9/WBRQ/8PxS//lTQKJfF27:nw1OfMGxRoiuWZ1jUx9qrS3lsC27
dix_16_xp.exe --> SHA256: 6c7eda3f5e9bbc685b0eefde2a51f0ccb06ad33805e617876a5124410cac9945
SSDEEP: 24576:Sx7USQ2bEdBF4XUCAdbpH7KYlvnIVGDDUWuXrO0VY/QjFdIkyoRn:MISXu5C47KMIaDWVY/QZdjpB
E-Mail Addresses
Ctorsenoria@tutanota[.]com
Folieloi@protonmail[.]com
mrromber@cock[.]li
mrromber@tutanota[.]com
sambolero@tutanoa[.]com
rightcheck@cock[.]li
fartcool@protonmail[.]ch
bestcool@keemail[.]me
tanoss@protonmail[.]com
sypress@protonmail[.]com
Associated Files
svchostt.exe
HOW_TO_OPEN_FILES.html
Advanced Port Scanner 2.4.2750.exe
d_upd1008.exe
NetworkShare_pre2.exe
PsExec64.exe (legitimate)
PsExec.exe (legitimate)
b.bat
NetworkShare.exe
kamikadze/32.exe
kamikadze/64.exe
kamikadze/64_log.txt
kamikadze/dump.bat
kamikadze/mimidrv (2).sys
kamikadze/mimilib (2).dll
kamikadze/86_log.txt
kamikadze/mimidrv.sys
kamikadze/mimilib.dll
Registry Keys
HKCU\SOFTWARE\Medusa
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\ --> EnableLinkedConnections = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System --> ConsentPromptBehaviorAdmin = 5
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System --> EnableLUA = 1
Ransomnote
All your data are encrypted!
What happened?
Your files are encrypted, and currently unavailable.
You can check it: all files on you computer has new expansion.
By the way, everything is possible to recover (restore), but you need to buy a unique decryptor.
Otherwise, you never cant return your data.
For purchasing a decryptor contact us by email:
mrromber@cock.li
If you will get no answer within 24 hours contact us by our alternate emails:
mrromber@tutanota.com
What guarantees?
Its just a business. If we do not do our work and liabilities - nobody will not cooperate with us.
To verify the possibility of the recovery of your files we can decrypted 1 file for free.
Attach 1 file to the letter (no more than 10Mb). Indicate your personal ID on the letter:
54E87CD3C1529DD06EB22FF80C49B5374ABB8E5B30D06E13BBE2E81411234A20DF1ADA53FDA68BD6294C96DAC3049B4BDC502706C0265B666946CD5ACB9E07D4
FE764BF468AF1A029B41162759D6164EB0652E95D3FAE3939773B505073E6090079C9C9243EE8B96AEB41A43B787B47DD01D7E192CEA0FB4FF72B5B6306C
425E042C6CBDE89BB5F2E7F9CC6601BD9430E87B42A56BEEFF207F20F9E4E5E48FA3274AE0DE8D65EEC0F2BA2CC4AECB22A9E80DC26BA84A849794E54B67
6FD2B21FF152A6A11BD86D063A965C1571078A439C97D52215738104F7B6EF7415CC4A2C03260BCB9A84E71E0883268747743893B2C334A38F9BCD34E5F9
39CFF3002697B8AD04E01A6B6DC0A460F4273778429962A7AEECEE3BA16A577A6B1D6B67A7FAEFA5C9CB8BBCEFEDC3FF6B04E9FE1904B0EBCBC6B21719EB
BE5D37B69B42BBEE2EA0D00C7439858D2D9BD4A57B47F3E05EBF913F5FAB195AF0575DD345E84347A82010CDC4C0507C98687242FA147930BE75A4A14220
C61ED4091E4155585A687EAB73CBEA8ADA7B93B5EB67877CDD0E35C9116B8DCADD2038C4EEAC42302F3B787E54F8AD24012E4EB4D5A28F48C2450DD346C0
A89B3C32252BD438399FAE630A1E099E9D130E7EA7E042841B468FF00FCF86B9C07C054827EE76956211CE70FEB686EC19971816936EBF2F143F4C98F8B3
34C96D1D35DD713CA33774C4D5D0
Attention!
- Attempts of change files by yourself will result in a loose of data.
- Our e-mail can be blocked over time. Write now, loss of contact with us will result in a loose of data.
- Use any third party software for restoring your data or antivirus solutions will result in a loose of data.
- Decryptors of other users are unique and will not fit your files and use of those will result in a loose of data.
- If you will not cooperate with our service - for us, its does not matter. But you will lose your time and data, cause just we have the private key.
Medusa Icon made by Freepik from www.flaticon.com

